Registration/SSH/SSH-FIDO2-Quick-Start: Difference between revisions
H Winkhardt (talk | contribs) m (typo) |
|||
| (3 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= SSH with |
= SSH with FIDO2 Security Keys - Quick Start Guide = |
||
This guide shows you how to secure your SSH keys with |
This guide shows you how to secure your SSH keys with FIDO2 security hardware keys (Yubikey, Feitian, Token2, etc.) using FIDO2. |
||
<div style="border: 3px solid #28a745; padding: 15px; background-color: #d4edda; margin: 10px 0;"> |
<div style="border: 3px solid #28a745; padding: 15px; background-color: #d4edda; margin: 10px 0;"> |
||
| Line 7: | Line 7: | ||
FIDO2 SSH keys (ED25519-SK) offer significant advantages: |
FIDO2 SSH keys (ED25519-SK) offer significant advantages: |
||
* |
* No 2-factor unlock required - work immediately after registration |
||
* |
* Hardware-protected - private key never leaves the Yubikey |
||
* |
* Physical presence required - you must touch the key to authenticate |
||
'''Note:''' ECDSA-SK keys are not supported on these clusters. Use ED25519-SK instead. |
'''Note:''' ECDSA-SK keys are not supported on these clusters. Use ED25519-SK instead. |
||
| Line 32: | Line 32: | ||
= Requirements = |
= Requirements = |
||
* A |
* A FIDO2 security key (e.g., Yubikey 5 series or newer, Feitian, Token2, etc.) |
||
* OpenSSH 8.2 or newer |
* OpenSSH 8.2 or newer |
||
* |
* For PIN setup: Either Chrome/Chromium/Brave browser OR <code>yubikey-manager</code> command-line tool (Yubikey only) |
||
* For SSH key generation: <code>openssh-client</code> package |
|||
'''Check your OpenSSH version:''' |
'''Check your OpenSSH version:''' |
||
| Line 46: | Line 47: | ||
= Quick Start Guide = |
= Quick Start Guide = |
||
== Step 1: Set up your |
== Step 1: Set up your FIDO2 Security Key == |
||
What is a FIDO2 PIN? The PIN protects your security key's FIDO2 functions. For Yubikeys, it's separate from any other PINs (like the PIV PIN). Choose a PIN you can remember or save it to a keystore - you have 8 attempts before needing to reset. |
|||
<div style="border: 3px solid #dc3545; padding: 15px; background-color: #f8d7da; margin: 10px 0;"> |
|||
Set a PIN for your Yubikey's FIDO2 functionality: |
|||
'''Important:''' |
|||
If you lose your FIDO2 PIN, the security key must be reset. '''All FIDO2 data will be lost,''' including SSH keys stored on the device. After reset, you must generate new SSH keys and re-register them. |
|||
</div> |
|||
=== Option A: Command Line Setup (Yubikey only) === |
|||
For Yubikeys, set a PIN using the <code>yubikey-manager</code> tool: |
|||
<pre> |
<pre> |
||
| Line 56: | Line 65: | ||
</pre> |
</pre> |
||
You'll be asked to enter a new PIN |
You'll be asked to '''enter a new PIN'''. |
||
'''Forgot your PIN or need to reset?''' You can reset your FIDO2 PIN using <code>ykman fido reset</code> or use the "Reset your security key" option shown in the browser security key settings (see image in Option B below). |
|||
=== Option B: Browser Setup (Chrome/Chromium/Brave) === |
|||
You can also set a FIDO2 PIN using Chrome, Chromium, or Brave browser. '''This method works for all FIDO2 security hardware keys''' (Yubikey, Feitian, Token2, etc.), not just Yubikeys. |
|||
| ⚫ | |||
'''1. Open Security Key Settings:''' |
|||
Enter the following in your browser's address bar: |
|||
* Chrome/Chromium/Brave: <code>chrome://settings/securityKeys</code> |
|||
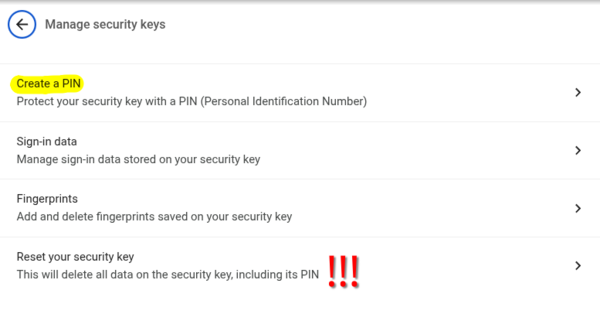
[[File:Chrome_Fido2_1.png|center|600px|thumb|Manage security keys - shows options for Create PIN, Sign-in data, Fingerprints, and Reset security key]] |
|||
'''Note:''' The "Reset your security key" option (shown with red warning icons in the image above) can be used if you forget your PIN. '''Warning: Reset will delete all FIDO2 data including SSH keys!''' |
|||
'''2. Create a PIN:''' |
|||
Click '''Create a PIN''' and follow the prompts: |
|||
[[File:Chrome_Fido2_2.png|center|400px|thumb|Create PIN dialog]] |
|||
| ⚫ | |||
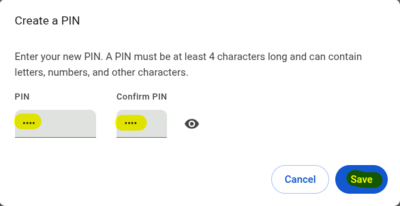
[[File:Chrome_Fido2_3.png|center|400px|thumb|Enter new PIN]] |
|||
'''3. PIN Created Successfully:''' |
|||
'''Forgot your PIN or need to reset?''' See the [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#troubleshooting troubleshooting guide]. |
|||
== Step 2: Create an SSH Key == |
== Step 2: Create an SSH Key == |
||
This creates a non-discoverable FIDO2 SSH key. The private key material is wrapped/encrypted with a secret stored on your security key - the security key is required for every authentication, but the actual key credentials are stored on your computer. |
|||
'''Note:''' For keys stored directly on the |
'''Note:''' For keys stored directly on the security key (resident/discoverable keys), see the [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#creating-discoverable-ssh-keys resident keys documentation]. |
||
Connect your |
'''Connect your FIDO2 security key''' and create a new SSH key. Optional: Choose a descriptive filename like <code>id_ed25519_sk_bwunicluster</code> or <code>id_ed25519_sk_nemo2</code>: |
||
<pre> |
<pre> |
||
ssh-keygen -t ed25519-sk |
ssh-keygen -t ed25519-sk -f ~/.ssh/id_ed25519_sk_bwunicluster |
||
</pre> |
</pre> |
||
When prompted: |
When prompted: |
||
* '''Enter PIN:''' First, you'll be asked to enter your FIDO2 PIN (the one you set in Step 1) |
* '''Enter PIN:''' First, you'll be asked to enter your FIDO2 PIN (the one you set in Step 1) |
||
| ⚫ | |||
* '''Filename:''' Choose a descriptive name like <code>id_ed25519_sk_bwunicluster</code> or <code>id_ed25519_sk_nemo2</code> |
|||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
Two files are created: |
Two files are created: |
||
* <code>~/.ssh/id_ed25519_sk_bwunicluster</code> - key handle (encrypted credentials that require the |
* <code>~/.ssh/id_ed25519_sk_bwunicluster</code> - key handle (encrypted credentials that require the security key) |
||
* <code>~/.ssh/id_ed25519_sk_bwunicluster.pub</code> - public key (this is what you'll upload) |
* <code>~/.ssh/id_ed25519_sk_bwunicluster.pub</code> - public key (this is what you'll upload) |
||
'''Want keys stored on the |
'''Want keys stored on the security key itself?''' See [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#creating-discoverable-ssh-keys resident keys documentation] for discoverable keys that can be copied to any machine. |
||
== Step 3: Register Your Public Key == |
== Step 3: Register Your Public Key == |
||
| Line 107: | Line 137: | ||
* Add your public key in bwIDM/bwServices |
* Add your public key in bwIDM/bwServices |
||
* Register it as an '''Interactive Key''' for your cluster |
* Register it as an '''Interactive Key''' for your cluster |
||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
After registering your key as an '''Interactive Key''' in bwIDM: |
After registering your key as an '''Interactive Key''' in bwIDM: |
||
| Line 118: | Line 149: | ||
'''What to expect:''' |
'''What to expect:''' |
||
1. Your |
1. Your security key will blink or light up |
||
2. Touch it to authenticate |
2. Touch it to authenticate |
||
3. You're logged in - no password needed! |
3. You're logged in - no password needed! |
||
| Line 125: | Line 156: | ||
<pre> |
<pre> |
||
Host bwuni |
Host bwuni bwunicluster.scc.kit.edu |
||
HostName bwunicluster.scc.kit.edu |
HostName bwunicluster.scc.kit.edu |
||
User fr_user1234 |
User fr_user1234 |
||
IdentityFile ~/.ssh/id_ed25519_sk_bwunicluster |
IdentityFile ~/.ssh/id_ed25519_sk_bwunicluster |
||
Host nemo2 |
Host nemo2 login.nemo.uni-freiburg.de |
||
HostName login.nemo.uni-freiburg.de |
HostName login.nemo.uni-freiburg.de |
||
User fr_user1234 |
User fr_user1234 |
||
| Line 142: | Line 173: | ||
= Advanced Topics = |
= Advanced Topics = |
||
== Using Multiple |
== Using Multiple Security Keys (Optional) == |
||
Having backup security keys adds convenience - you can switch between devices without reconfiguring. |
|||
'''Note:''' If you lose your |
'''Note:''' If you lose your security key, you can still access the cluster using regular SSH keys (with 2FA unlock) or password login with TOTP. |
||
'''Setup:''' |
'''Setup:''' |
||
1. Create a key on your first |
1. Create a key on your first security key: <code>id_ed25519_sk_key1</code> |
||
2. Create another key on your second |
2. Create another key on your second security key: <code>id_ed25519_sk_key2</code> |
||
3. Register '''both public keys''' in bwIDM as Interactive Keys |
3. Register '''both public keys''' in bwIDM as Interactive Keys |
||
4. Configure <code>~/.ssh/config</code> with multiple identities: |
4. Configure <code>~/.ssh/config</code> with multiple identities: |
||
<pre> |
<pre> |
||
Host bwunicluster.scc.kit.edu uc*.scc.kit.edu login*.nemo.uni-freiburg.de |
|||
Host bwuni nemo2 |
|||
User fr_user1234 |
User fr_user1234 |
||
IdentityFile ~/.ssh/id_ed25519_sk_key1 |
IdentityFile ~/.ssh/id_ed25519_sk_key1 |
||
| Line 162: | Line 193: | ||
</pre> |
</pre> |
||
SSH will automatically try each key until it finds one with a connected |
SSH will automatically try each key until it finds one with a connected security key. |
||
= Troubleshooting = |
= Troubleshooting = |
||
| Line 169: | Line 200: | ||
* '''Key not working?''' |
* '''Key not working?''' |
||
** Make sure your |
** Make sure your security key is plugged in |
||
** Try unplugging and re-plugging the |
** Try unplugging and re-plugging the security key |
||
** Check if the key is blinking (requires touch) |
** Check if the key is blinking or lit up (requires touch) |
||
* '''Command not found?''' |
* '''Command not found?''' |
||
** Install <code>yubikey-manager</code>: |
** Install <code>yubikey-manager</code> (for Yubikey command-line setup only): |
||
*** Debian/Ubuntu: <code>sudo apt install yubikey-manager</code> |
*** Debian/Ubuntu: <code>sudo apt install yubikey-manager</code> |
||
*** RHEL/Rocky/Alma: <code>sudo dnf install yubikey-manager</code> |
*** Fedora/RHEL/Rocky/Alma: <code>sudo dnf install yubikey-manager</code> |
||
** Install <code>openssh-client</code> if missing |
** Install <code>openssh-client</code> if missing |
||
| Line 189: | Line 220: | ||
* '''PIN locked after too many attempts?''' |
* '''PIN locked after too many attempts?''' |
||
** Reset FIDO2 PIN: See [ |
** Reset FIDO2 PIN: See [[#Step_1:_Set_up_your_FIDO2_Security_Key|Step 1]] |
||
'''Need more help?''' See the [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#troubleshooting complete troubleshooting guide]. |
|||
= Learn More = |
= Learn More = |
||
| Line 202: | Line 231: | ||
** [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#creating-discoverable-ssh-keys Resident Keys] - Store keys directly on Yubikey |
** [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#creating-discoverable-ssh-keys Resident Keys] - Store keys directly on Yubikey |
||
** [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#ssh-configuration-for-fido2-secured-ssh-keys SSH Config Examples] - Automate your SSH connections |
** [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#ssh-configuration-for-fido2-secured-ssh-keys SSH Config Examples] - Automate your SSH connections |
||
** [https://gitlab.rz.uni-freiburg.de/escience-public/yubikey#yubikey-best-practices Backup Strategies] - Multi-key and recovery setups |
|||
'''Official Yubico Documentation:''' |
'''Official Yubico Documentation:''' |
||
Latest revision as of 15:30, 12 January 2026
SSH with FIDO2 Security Keys - Quick Start Guide
This guide shows you how to secure your SSH keys with FIDO2 security hardware keys (Yubikey, Feitian, Token2, etc.) using FIDO2.
Why FIDO2 SSH Keys?
FIDO2 SSH keys (ED25519-SK) offer significant advantages:
- No 2-factor unlock required - work immediately after registration
- Hardware-protected - private key never leaves the Yubikey
- Physical presence required - you must touch the key to authenticate
Note: ECDSA-SK keys are not supported on these clusters. Use ED25519-SK instead.
| Cluster | FIDO2 Support |
|---|---|
| bwUniCluster 3.0 | ✓ |
| bwForCluster BinAC 2 | ✗ |
| bwForCluster Helix | ✗ |
| bwForCluster JUSTUS 2 | ✗ |
| bwForCluster NEMO 2 | ✓ |
Requirements
- A FIDO2 security key (e.g., Yubikey 5 series or newer, Feitian, Token2, etc.)
- OpenSSH 8.2 or newer
- For PIN setup: Either Chrome/Chromium/Brave browser OR
yubikey-managercommand-line tool (Yubikey only) - For SSH key generation:
openssh-clientpackage
Check your OpenSSH version:
ssh -V ssh -Q PubkeyAcceptedAlgorithms | grep sk-ssh-ed25519@openssh.com
Need help with installation? See the detailed setup guide for your operating system.
Quick Start Guide
Step 1: Set up your FIDO2 Security Key
What is a FIDO2 PIN? The PIN protects your security key's FIDO2 functions. For Yubikeys, it's separate from any other PINs (like the PIV PIN). Choose a PIN you can remember or save it to a keystore - you have 8 attempts before needing to reset.
Important:
If you lose your FIDO2 PIN, the security key must be reset. All FIDO2 data will be lost, including SSH keys stored on the device. After reset, you must generate new SSH keys and re-register them.
Option A: Command Line Setup (Yubikey only)
For Yubikeys, set a PIN using the yubikey-manager tool:
ykman fido access change-pin
You'll be asked to enter a new PIN.
Forgot your PIN or need to reset? You can reset your FIDO2 PIN using ykman fido reset or use the "Reset your security key" option shown in the browser security key settings (see image in Option B below).
Option B: Browser Setup (Chrome/Chromium/Brave)
You can also set a FIDO2 PIN using Chrome, Chromium, or Brave browser. This method works for all FIDO2 security hardware keys (Yubikey, Feitian, Token2, etc.), not just Yubikeys. Alternative: For Yubikeys specifically, you can also use Yubico Authenticator.
1. Open Security Key Settings:
Enter the following in your browser's address bar:
- Chrome/Chromium/Brave:
chrome://settings/securityKeys
Note: The "Reset your security key" option (shown with red warning icons in the image above) can be used if you forget your PIN. Warning: Reset will delete all FIDO2 data including SSH keys!
2. Create a PIN:
Click Create a PIN and follow the prompts:
3. PIN Created Successfully:
Step 2: Create an SSH Key
This creates a non-discoverable FIDO2 SSH key. The private key material is wrapped/encrypted with a secret stored on your security key - the security key is required for every authentication, but the actual key credentials are stored on your computer.
Note: For keys stored directly on the security key (resident/discoverable keys), see the resident keys documentation.
Connect your FIDO2 security key and create a new SSH key. Optional: Choose a descriptive filename like id_ed25519_sk_bwunicluster or id_ed25519_sk_nemo2:
ssh-keygen -t ed25519-sk -f ~/.ssh/id_ed25519_sk_bwunicluster
When prompted:
- Enter PIN: First, you'll be asked to enter your FIDO2 PIN (the one you set in Step 1)
- Passphrase: Press Enter to skip - the key is protected by requiring physical security key presence
- Touch your security key: The key will blink or light up - touch it to confirm
Two files are created:
~/.ssh/id_ed25519_sk_bwunicluster- key handle (encrypted credentials that require the security key)~/.ssh/id_ed25519_sk_bwunicluster.pub- public key (this is what you'll upload)
Want keys stored on the security key itself? See resident keys documentation for discoverable keys that can be copied to any machine.
Step 3: Register Your Public Key
FIDO2 SSH Keys work immediately without 2-factor authentication!
Unlike regular SSH keys, FIDO2 keys do not need to be "unlocked" with username/password. They work as soon as you register them as Interactive Keys.
For bwUniCluster 3.0 and bwForCluster NEMO 2:
1. View your public key:
cat ~/.ssh/id_ed25519_sk_bwunicluster.pub
2. Copy the complete output (starts with sk-ssh-ed25519@openssh.com)
3. Follow the SSH Key Registration Guide to:
- Add your public key in bwIDM/bwServices
- Register it as an Interactive Key for your cluster
That's it! You can connect immediately - no 2FA unlock needed.
Step 4: Connect with Your Security Key
After registering your key as an Interactive Key in bwIDM:
ssh -i ~/.ssh/id_ed25519_sk_bwunicluster your_username@bwunicluster.scc.kit.edu
What to expect: 1. Your security key will blink or light up 2. Touch it to authenticate 3. You're logged in - no password needed!
Tip: Add your key to ~/.ssh/config to avoid typing the -i option every time:
Host bwuni bwunicluster.scc.kit.edu HostName bwunicluster.scc.kit.edu User fr_user1234 IdentityFile ~/.ssh/id_ed25519_sk_bwunicluster Host nemo2 login.nemo.uni-freiburg.de HostName login.nemo.uni-freiburg.de User fr_user1234 IdentityFile ~/.ssh/id_ed25519_sk_nemo2
Then simply connect with: ssh bwuni or ssh nemo2
See SSH config examples for more advanced configurations.
Advanced Topics
Using Multiple Security Keys (Optional)
Having backup security keys adds convenience - you can switch between devices without reconfiguring.
Note: If you lose your security key, you can still access the cluster using regular SSH keys (with 2FA unlock) or password login with TOTP.
Setup:
1. Create a key on your first security key: id_ed25519_sk_key1
2. Create another key on your second security key: id_ed25519_sk_key2
3. Register both public keys in bwIDM as Interactive Keys
4. Configure ~/.ssh/config with multiple identities:
Host bwunicluster.scc.kit.edu uc*.scc.kit.edu login*.nemo.uni-freiburg.de User fr_user1234 IdentityFile ~/.ssh/id_ed25519_sk_key1 IdentityFile ~/.ssh/id_ed25519_sk_key2
SSH will automatically try each key until it finds one with a connected security key.
Troubleshooting
Common Issues:
- Key not working?
- Make sure your security key is plugged in
- Try unplugging and re-plugging the security key
- Check if the key is blinking or lit up (requires touch)
- Command not found?
- Install
yubikey-manager(for Yubikey command-line setup only):- Debian/Ubuntu:
sudo apt install yubikey-manager - Fedora/RHEL/Rocky/Alma:
sudo dnf install yubikey-manager
- Debian/Ubuntu:
- Install
openssh-clientif missing
- Install
- Old OpenSSH?
- Check version:
ssh -V - Update to version 8.2 or newer
- On older systems, consider using a newer OpenSSH version or upgrade your OS
- Check version:
- "invalid format" or "unknown key type"?
- Your OpenSSH version is too old (needs 8.2+)
- The cluster doesn't support FIDO2 keys (only bwUniCluster 3.0 and NEMO 2)
- PIN locked after too many attempts?
- Reset FIDO2 PIN: See Step 1
Learn More
Cluster-Specific Documentation:
Yubikey & FIDO2 SSH Documentation:
- Comprehensive Yubikey Guide - Setup, configuration, troubleshooting
- Resident Keys - Store keys directly on Yubikey
- SSH Config Examples - Automate your SSH connections
Official Yubico Documentation:
- Securing SSH with FIDO2 - Technical deep dive