BwUniCluster 2.0 User Access/SSH Keys
SSH Keys are a mechanism for logging into a computer system without having to enter a password. Instead of authenticating yourself with something you know (a password), you prove your identity by showing the server something you have (a cryptographic key).
The usual process is the following:
- The user generates a pair of SSH Keys, a private key and a public key, on their local system. The private key never leaves the local system.
- The user then logs into the remote system using the remote system password and adds the public key to a file called ~/.ssh/authorized_keys .
- All following logins will no longer require the entry of the remote system password because the local system can prove to the remote system that it has a private key matching the public key on file.
While SSH Keys have many advantages, the concept also has a number of issues which make it hard to handle them securely:
- The private key on the local system is supposed to be protected by a strong passphrase. There is no possibility for the server to check if this is the case. Many users do not use a strong passphrase or do not use any passphrase at all. If such a private key is stolen, an attacker can immediately use it to access the remote system.
- There is no concept of validity. Users are not forced to regularly generate new SSH Key pairs and replace the old ones. Often the same key pair is used for many years and the users have no overview of how many systems they have stored their SSH Keys on.
- SSH Keys can be restricted so they can only be used to execute specific commands on the server, or log in from specified IP addresses. Most users do not do this.
To fix these issues it is no longer possible to self-manage your SSH Keys by adding them to the ~/.ssh/authorized_keys file on bwUniCluster. SSH Keys have to be managed via the central bwIDM system instead. Existing authorized_keys files are ignored.
Contents
1 Minimum requirements for SSH Keys
Algorithms and Key sizes:
- 3096 bits or more for RSA
- 521 bits for ECDSA
- 256 Bits (Default) for ED25519
ECDSA-SK and ED25519-SK keys (for use with U2F Hardware Tokens) cannot be used yet.
2 Adding a new SSH Key
1. Log into https://bwidm.scc.kit.edu.
2. Click on My SSH Pubkeys or Meine SSH Pubkeys in the Main Menu.
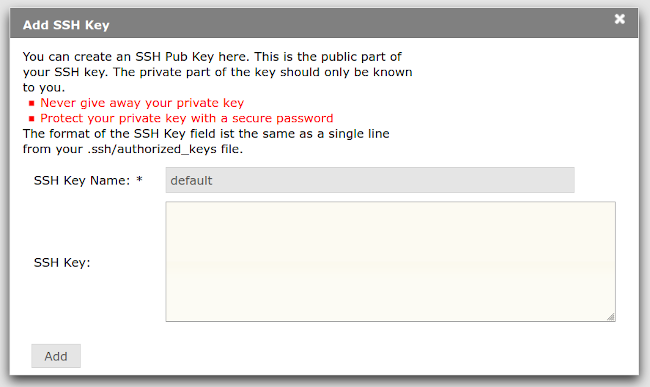
3. Click on the Add SSH Key or SSH Key hochladen button.
4. A new window will appear. Enter a name for the key and paste your SSH public key (NOT the private key!) into the box labelled "SSH Key:". Click on the button labelled Add or Hinzufügen. 'Note that you cannot add an SSH public key that has already been used before.
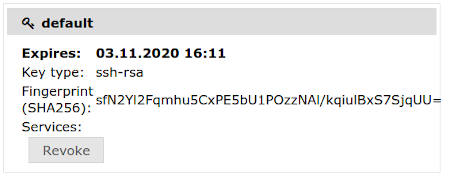
5. If everything worked fine your new key will show up in the user interface:
Newly added keys have a validity of three months. After that they will be revoked and put on a blocklist, so they cannot be used again.
3 Registering an Interactive Key
4 Registering a Command Key