Registration/SSH
|
This guide applies ONLY to: bwUniCluster 3.0 • bwForCluster Helix • bwForCluster NEMO 2 On all other clusters, SSH keys are still managed via |
Registering SSH Keys with your Cluster
SSH Keys allow you to log into a system without entering a password. Instead of proving your identity with something you know (a password), you prove it with something you have (a cryptographic key).
Why SSH Key Management?
On bwUniCluster 3.0, bwForCluster Helix, and bwForCluster NEMO 2, SSH keys must be managed through bwIDM/bwServices for security reasons:
- Security enforcement: Ensures keys use strong algorithms and have limited validity (180 days)
- Centralized management: All keys can be reviewed and revoked from one location
- Two types available: Interactive keys (for manual logins) and Command keys (for automated workflows)
Note: Self-managed ~/.ssh/authorized_keys files are ignored on these clusters.
SSH Key Requirements
Supported Algorithms and Key Sizes
- RSA: 2048 bits or more
- ECDSA: 521 bits
- ED25519: 256 bits (default, recommended)
- ECDSA-SK / ED25519-SK: FIDO2 hardware keys (Yubikey, etc.)
Important: Always protect your private keys with a strong passphrase.
FIDO2 Hardware Keys (Recommended)
|
FIDO2 SSH Keys (ECDSA-SK and ED25519-SK) offer the best security:
See SSH with Yubikey - Quick Start Guide for setup instructions. |
|
FIDO2 SSH Keys currently work ONLY on: bwUniCluster 3.0 and bwForCluster NEMO 2 NOT supported on bwForCluster Helix! |
Adding a new SSH Key
|
SSH keys are managed via the My SSH Pubkeys menu on your cluster's registration page:
1. Navigate to your cluster's SSH key management:
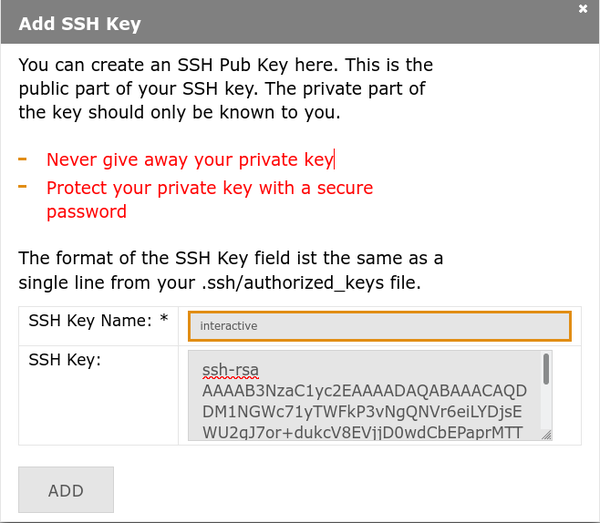
2. Click Add SSH Key / SSH Key Hochladen
3. Enter key details:
- Name: Descriptive name for your key (e.g., "laptop-work")
- SSH Key: Paste the complete contents of your
.pubfile - Click Add / Hinzufügen
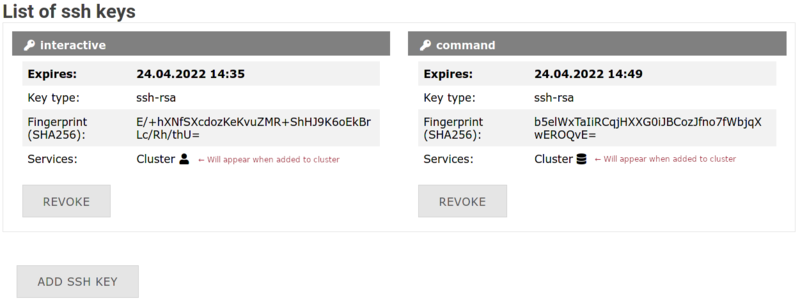
4. Confirmation: Your new key appears in the list
Next step: Bind your key to a service as either an Interactive Key (manual logins) or Command Key (automated workflows).
Registering an Interactive Key
Interactive Keys are used for manual SSH logins to work on the cluster.
Key Validity and 2-Factor Authentication
|
Regular SSH Keys require 2-factor unlock:
FIDO2 SSH Keys (ECDSA-SK/ED25519-SK) work differently:
|
| Cluster | Validity after 2FA Login |
|---|---|
| bwUniCluster 3.0 | 8 hours |
| bwForCluster Helix | 12 hours |
| bwForCluster NEMO 2 | 12 hours |
Registration Steps
1. Add your SSH key if not already done
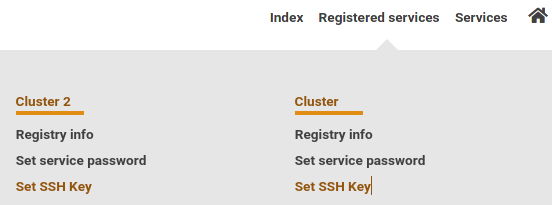
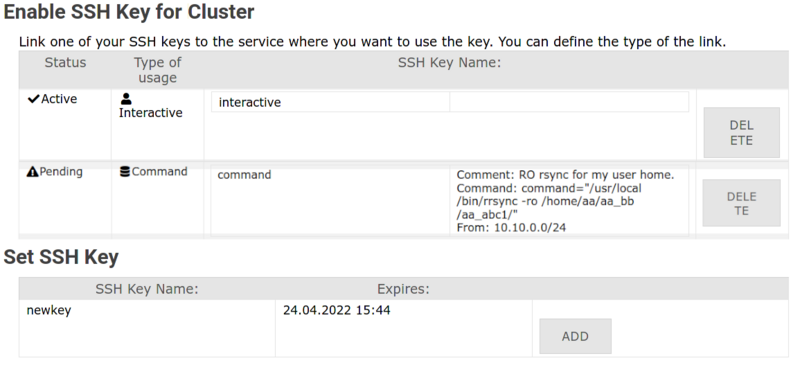
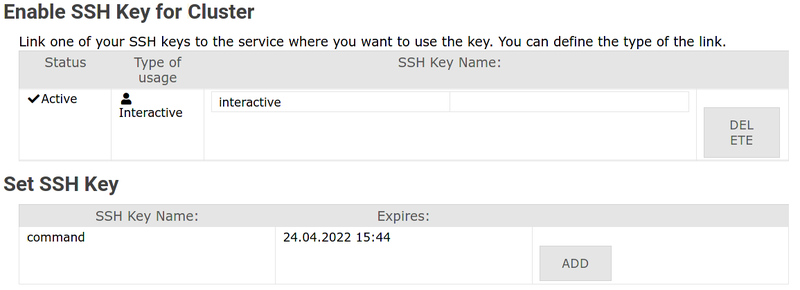
2. Navigate to Registered Services / Registrierte Dienste → Click Set SSH Key / SSH Key setzen for your cluster
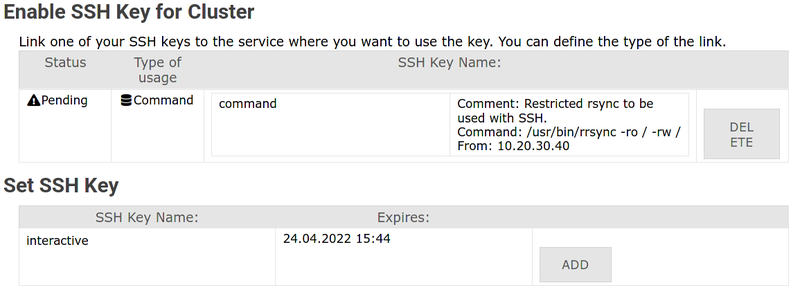
3. Find your key in the bottom section → Click Add / Hinzufügen
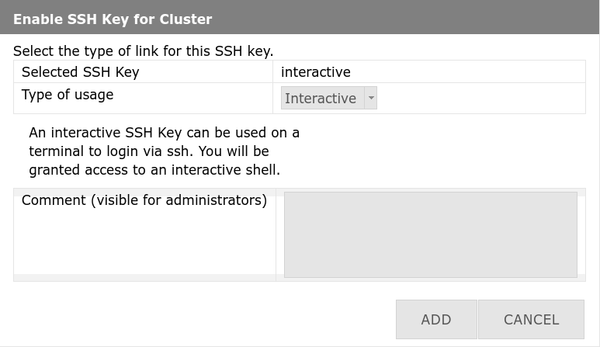
4. Select Interactive as usage type → Add optional comment → Click Add / Hinzufügen
5. Done! Your key is now active for interactive logins
Registering a Command Key
Command Keys enable automated workflows without manual login (e.g., automated backups, data transfers).
Security Requirements
|
Command keys are always valid (no 2FA required), making them high-value targets. Mandatory restrictions:
|
Common use case: For rsync data transfers, see the rrsync wiki guide.
Registration Steps
1. Add your SSH key if not already done
2. Navigate to Registered Services → Click Set SSH Key for your cluster
3. Find your key in the bottom section → Click Add / Hinzufügen
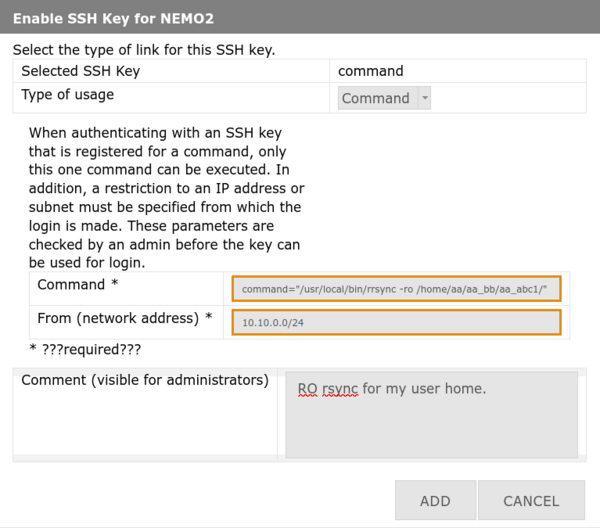
4. Configure command restrictions:
- Usage type: Select Command
- Command: Enter full path and parameters (example for rrsync below)
- From: Specify IP address, range, or subnet (see man 8 sshd)
- Comment: Explain purpose (speeds up approval)
- Click Add / Hinzufügen
| Example: rrsync for automated data transfer |
|---|
/usr/local/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/ Note: Verify the exact path on your cluster first (may be |
5. Wait for approval: Key status shows Pending until an administrator approves it
You'll receive an email when the key is approved and ready to use.
Revoking SSH Keys
Revoked keys are immediately disabled and cannot be reused.
1. Navigate to your cluster's SSH key management:
2. Click REVOKE / ZURÜCKZIEHEN next to the key you want to disable