Registration/2FA: Difference between revisions
| (13 intermediate revisions by 5 users not shown) | |||
| Line 5: | Line 5: | ||
[[Image:Attention.svg|center|25px]] |
[[Image:Attention.svg|center|25px]] |
||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|style="padding:5px; background:#cef2e0; text-align:left"| |
||
You |
You or your group must take care of the hardware for the second factor yourself. We do not provide hardware keys or mobile devices. |
||
|} |
|} |
||
To improve security a '''2-factor authentication mechanism (2FA)''' is being enforced for logins to bwUniCluster/bwForClusters. In addition to the service password a second value, the '''second factor''', has to be entered on every login. |
To improve security a '''2-factor authentication mechanism (2FA)''' is being enforced for logins to bwUniCluster/bwForClusters. In addition to the service password a second value, the '''second factor''', has to be entered on every login. |
||
If you only have a mobile device, you can use software-based solutions as a second factor. If you don't want to use a smartphone app, we recommend using a hardware token such as Yubikey |
If you only have a mobile device, you can use software-based solutions as a second factor. If you don't want to use a smartphone app, we recommend using a hardware token such as Yubikey. |
||
* If you have any questions about 2FA, please read the [[Registration/2FA/FAQ|FAQs]], and if your question remains unanswered, please submit a support ticket. |
|||
| ⚫ | |||
* The Pros and Cons of the various solutions can be found in this [[Registration/2FA/ProCon|wiki]]. |
|||
| ⚫ | |||
{|style="background:#deffee; width:100%;" |
{|style="background:#deffee; width:100%;" |
||
| Line 36: | Line 40: | ||
The most common solution is to use a mobile device (e.g. your smartphone or tablet) as a Software Token by installing one of the following apps: |
The most common solution is to use a mobile device (e.g. your smartphone or tablet) as a Software Token by installing one of the following apps: |
||
* 2FAS for [https://play.google.com/store/apps/details?id=com.twofasapp Android] or [https://apps.apple.com/us/app/2fa-authenticator-2fas/id1217793794 iOS] ([https://2fas.com/ Web Page] and [https://github.com/twofas GitHub], ''Apple and Google Cloud can be used for backups depending on the operating system.'') |
* 2FAS for [https://play.google.com/store/apps/details?id=com.twofasapp Android] or [https://apps.apple.com/us/app/2fa-authenticator-2fas/id1217793794 iOS] ([https://2fas.com/ Web Page] and [https://github.com/twofas GitHub], ''Apple and Google Cloud can be used for backups depending on the operating system.'') |
||
* Open Source FreeOTP ([https://github.com/freeotp GitHub]) on [https://f-droid.org/en/packages/org.fedorahosted.freeotp/ F-Droid], [https://play.google.com/store/search?q=freeotp Android] or [https://apps.apple.com/de/app/freeotp-authenticator/id872559395 iOS] with a possibility of local backup files. |
|||
* Google Authenticator for [https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2 Android] or [https://apps.apple.com/de/app/google-authenticator/id388497605 iOS] (''Google Cloud can be used for backups, but these backups are not encrypted and can therefore be read by Google!'') |
* Google Authenticator for [https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2 Android] or [https://apps.apple.com/de/app/google-authenticator/id388497605 iOS] (''Google Cloud can be used for backups, but these backups are not encrypted and can therefore be read by Google!'') |
||
* Microsoft Authenticator for [https://play.google.com/store/apps/details?id=com.azure.authenticator Android] or [https://apps.apple.com/de/app/microsoft-authenticator/id983156458 iOS] ([https://www.microsoft.com/de-de/security/mobile-authenticator-app Web Page]) |
* Microsoft Authenticator for [https://play.google.com/store/apps/details?id=com.azure.authenticator Android] or [https://apps.apple.com/de/app/microsoft-authenticator/id983156458 iOS] ([https://www.microsoft.com/de-de/security/mobile-authenticator-app Web Page]) |
||
* LastPass Authenticator for [https://play.google.com/store/apps/details?id=com.lastpass.authenticator Android], [https://apps.apple.com/us/app/lastpass-authenticator/id1079110004 iOS] or [https://lastpass.com/auth/ Windows] |
* LastPass Authenticator for [https://play.google.com/store/apps/details?id=com.lastpass.authenticator Android], [https://apps.apple.com/us/app/lastpass-authenticator/id1079110004 iOS] or [https://lastpass.com/auth/ Windows] |
||
* Aegis Authenticator for [https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis Android (Google Play)] or [https://f-droid.org/en/packages/com.beemdevelopment.aegis/ Android (F-Droid)] ([https://getaegis.app/ Web Page]) |
* Aegis Authenticator for [https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis Android (Google Play)] or [https://f-droid.org/en/packages/com.beemdevelopment.aegis/ Android (F-Droid)] ([https://getaegis.app/ Web Page]) |
||
* andOTP Authenticator for [https://play.google.com/store/apps/details?id=org.shadowice.flocke.andotp Android (Google Play)] or [https://f-droid.org/packages/org.shadowice.flocke.andotp/ Android (F-Droid)] ([https://github.com/andOTP/andOTP GitHub]) |
|||
* OTP Auth for [https://apps.apple.com/app/otp-auth/id659877384 iOS] |
* OTP Auth for [https://apps.apple.com/app/otp-auth/id659877384 iOS] |
||
* (''Authy for [https://play.google.com/store/apps/details?id=com.authy.authy Android], [https://apps.apple.com/us/app/authy/id494168017 iOS], [https://authy.com/download/ Mac, Windows or Linux], requires account'') |
* (''Authy for [https://play.google.com/store/apps/details?id=com.authy.authy Android], [https://apps.apple.com/us/app/authy/id494168017 iOS], [https://authy.com/download/ Mac, Windows or Linux], requires account'') |
||
| Line 65: | Line 69: | ||
To activate the second factor, '''please perform the following steps:''' |
To activate the second factor, '''please perform the following steps:''' |
||
1. '''Select the registration server of the cluster''' for which you want to create a second factor and login to it:</br> → [https://login.bwidm.de/user/twofa.xhtml Registration server for '''bwUniCluster 2.0''', '''bwForCluster JUSTUS 2''' and '''bwForCluster NEMO'''] (2FA tokens are valid for all three clusters; KIT members can reuse their existing hardware and software tokens)</br> → [https://bwservices.uni-heidelberg.de |
1. '''Select the registration server of the cluster''' for which you want to create a second factor and login to it:</br> → [https://login.bwidm.de/user/twofa.xhtml Registration server for '''bwUniCluster 2.0''', '''bwForCluster JUSTUS 2''' and '''bwForCluster NEMO 2'''] (2FA tokens are valid for all three clusters; KIT members can reuse their existing hardware and software tokens)</br> → [https://bwservices.uni-heidelberg.de/user/twofa.xhtml Registration server for '''bwForCluster Helix'''] |
||
[[File:BwIDM-twofa.png|center|600px|thumb|My Tokens]] |
[[File:BwIDM-twofa.png|center|600px|thumb|My Tokens]] |
||
2. '''Register a new "[[Registration/2FA#Registering_a_new_Software_Token_using_a_Mobile_APP|Smartphone Token]]"''' or if you own a [https://www.yubico.com/ Yubikey]''' register a new "[[Registration/2FA#Registering_a_new_Yubikey_OTP_Token|Yubikey Token]]"''' or '''"[[Registration/2FA#Registering_a_new_Yubikey_OATH_TOTP_Token|Yubikey OATH TOTP Token]]"''' |
2. '''Register a new "[[Registration/2FA#Registering_a_new_Software_Token_using_a_Mobile_APP|Smartphone Token]]"''' or if you own a [https://www.yubico.com/ Yubikey]''' register a new "[[Registration/2FA#Registering_a_new_Yubikey_OTP_Token|Yubikey Token]]"''' or '''"[[Registration/2FA#Registering_a_new_Yubikey_OATH_TOTP_Token|Yubikey OATH TOTP Token]]"'''. |
||
3. '''Register a new "[[Registration/2FA#Backup_TAN_List|TAN List]]" (backup TAN list)'''. |
3. '''Register a new "[[Registration/2FA#Backup_TAN_List|TAN List]]" (backup TAN list)'''. |
||
| Line 104: | Line 108: | ||
The exact process is a little bit different in every app, but is usually started by pressing on a button with a plus (+) sign or an icon of a QR code. |
The exact process is a little bit different in every app, but is usually started by pressing on a button with a plus (+) sign or an icon of a QR code. |
||
5. Once the QR code has been loaded into your Software Token app there should be a new entry called '''bwIDM''' (bwUniCluster, JUSTUS 2 and |
5. Once the QR code has been loaded into your Software Token app there should be a new entry called '''bwIDM''' (bwUniCluster, JUSTUS 2 and NEMO2) or '''bwServices''' (Helix). |
||
Generate an One-Time-Password by pressing on this entry or selecting the appropriate button/menu item. |
Generate an One-Time-Password by pressing on this entry or selecting the appropriate button/menu item. |
||
You will receive a six-digit code. |
You will receive a six-digit code. |
||
| Line 245: | Line 249: | ||
'''If you no longer have valid tokens (mobile app, hardware token, Yubikey or backup TAN, i.e. lost or broken smartphone), you can not access the section "My Tokens" anymore. |
'''If you no longer have valid tokens (mobile app, hardware token, Yubikey or backup TAN, i.e. lost or broken smartphone), you can not access the section "My Tokens" anymore. |
||
In this case you will need to contact the [https:// |
In this case you will need to contact the [https://www.bwhpc.de/supportportal ticket system].''' |
||
Open a ticket, include your user name, the name of the bwHPC cluster and ask for a reset of your 2FA tokens. |
Open a ticket, include your user name, the name of the bwHPC cluster and ask for a reset of your 2FA tokens. |
||
Please note that this process may take some time and also means additional work for the operators. |
Please note that this process may take some time and also means additional work for the operators. |
||
= Pros and Cons of the different Solutions = |
|||
This section briefly describes the differences between the above solutions. |
|||
== Mobile App == |
|||
This sections describes the pros and cons of an app on your mobile device (phone or tablet). |
|||
'''Pros:''' |
|||
* Can be used at no extra cost if you have a mobile device. |
|||
* When using your cell phone, you always have the second factor at your fingertips. |
|||
'''Cons:''' |
|||
* You need a mobile device. |
|||
* If your device is lost or damaged, you will lose your second factor. (''Some services offer cloud synchronization, but you usually need an account and Google Authenticator does not encrypt your TOTP secret keys when storing them in the cloud.'') |
|||
== Yubico OTP == |
|||
This sections describes the pros and cons of Yubico OTP. For Yubico OTP to work, you need a Yubikey with Yubico OTP support. |
|||
'''Pros:''' |
|||
* You do not need a mobile device. All you need is a USB port. |
|||
* Simple and fast: The Yubikeys are preconfigured for Yubico OTP. All you need to do is touch the metal plate on the device when prompted. |
|||
'''Cons:''' |
|||
* You have to spend money on a Yubikey. |
|||
* If you lose the device, you will lose the second factor (it is recommended to buy at least two Yubikeys). |
|||
* If you do not have your Yubikey with you, you cannot log in to the clusters. |
|||
* In bwHPC, the Yubicloud is used to synchronize the Yubico OTP keys (third-party provider). |
|||
== Yubikey OATH TOTP == |
|||
This sections describes the pros and cons of Yubikey OATH TOTP. For Yubikey OATH TOTP to work, you need a Yubikey with OATH TOTP support. This solution is similar to the one for mobile apps, but an external pin generator is used. |
|||
'''Pros:''' |
|||
* You do not need a mobile device. All you need is a USB port. |
|||
* You can use multiple devices such as phones and tablets (via USB, Lightning or NFC) or even your computer(s). |
|||
* Since the TOTP is calculated on the Yubikey and the computer/mobile device is only used for displaying the TOTP and time synchronization, you can use the same device you use for login. |
|||
'''Cons:''' |
|||
* You have to spend money on a Yubikey. |
|||
* If you lose the device, you will lose the second factor (it is recommended to buy at least two Yubikeys). |
|||
* If you do not have your Yubikey with you, you cannot log in to the clusters. |
|||
Latest revision as of 14:58, 30 June 2025
Generate a Second Factor (2FA)
|
You or your group must take care of the hardware for the second factor yourself. We do not provide hardware keys or mobile devices. |
To improve security a 2-factor authentication mechanism (2FA) is being enforced for logins to bwUniCluster/bwForClusters. In addition to the service password a second value, the second factor, has to be entered on every login.
If you only have a mobile device, you can use software-based solutions as a second factor. If you don't want to use a smartphone app, we recommend using a hardware token such as Yubikey.
- If you have any questions about 2FA, please read the FAQs, and if your question remains unanswered, please submit a support ticket.
- The Pros and Cons of the various solutions can be found in this wiki.
How 2FA works on the bwHPC Clusters
|
It is very important that the device that generates the One-Time Passwords and the device which is used to log into the bwUniCluster/bwForClusters are not the same. Otherwise an attacker who gains access to your system can steal both the service password and the secret key of the Software Token application, which allows them to generate One-Time Passwords and log into the HPC system without your knowledge. |
On the bwUniCluster/bwForClusters we use either six-digit, auto-generated, time-dependent one-time passwords (TOTP) or Yubico OTP.
TOTPs are generated by a piece of software which is part of a special hardware device (a hardware token) or of a normal application running on a common device (a software token).
The Token has to be synchronized with a central server before it can be used for authentication and then generates an endless stream of six-digit values (TOTPs) which can only be used once and are only valid during a very short interval of time. This makes it much harder for potential attackers to access the HPC system, even if they know the regular service password.
Typically a new TOTP value is generated every 30 seconds. When the current TOTP value has once been used successfully for a login, it is depleted and one has to wait up to 30 seconds for the next TOTP value. If you don't want to use a smartphone, we recommend using a hardware token, such as Yubikey or another TOTP-compatible device. We do not recommend the use of TOTP generators for PCs. If the second factor is generated on the same computer on which the login takes place, it is no longer a second factor.
The most common solution is to use a mobile device (e.g. your smartphone or tablet) as a Software Token by installing one of the following apps:
- 2FAS for Android or iOS (Web Page and GitHub, Apple and Google Cloud can be used for backups depending on the operating system.)
- Open Source FreeOTP (GitHub) on F-Droid, Android or iOS with a possibility of local backup files.
- Google Authenticator for Android or iOS (Google Cloud can be used for backups, but these backups are not encrypted and can therefore be read by Google!)
- Microsoft Authenticator for Android or iOS (Web Page)
- LastPass Authenticator for Android, iOS or Windows
- Aegis Authenticator for Android (Google Play) or Android (F-Droid) (Web Page)
- OTP Auth for iOS
- (Authy for Android, iOS, Mac, Windows or Linux, requires account)
(These are only suggestions. You can use any application compatible with the TOTP standard.)
Yubico OTP is also supported if you want to use your Yubikey without depending on having a six-digit code displayed.
Token Management
|
bwUniCluster/bwForCluster Tokens are generally managed via the Index -> My Tokens menu entry on the registration pages for the clusters. Here you can register, activate, deactivate and delete tokens.
To activate the second factor, please perform the following steps:
1. Select the registration server of the cluster for which you want to create a second factor and login to it:
→ Registration server for bwUniCluster 2.0, bwForCluster JUSTUS 2 and bwForCluster NEMO 2 (2FA tokens are valid for all three clusters; KIT members can reuse their existing hardware and software tokens)
→ Registration server for bwForCluster Helix
2. Register a new "Smartphone Token" or if you own a Yubikey register a new "Yubikey Token" or "Yubikey OATH TOTP Token".
3. Register a new "TAN List" (backup TAN list).
4. Repeat step 2. for additional tokens.
Registering a new Software Token using a Mobile APP
|
Please disable all privacy tools, ad blockers and further add-ons when registering new tokens. |
1. Select the registration server of the cluster for which you want to create a second factor and login to it.
2. Registering a new Token starts with a click NEW SMARTPHONE TOKEN.
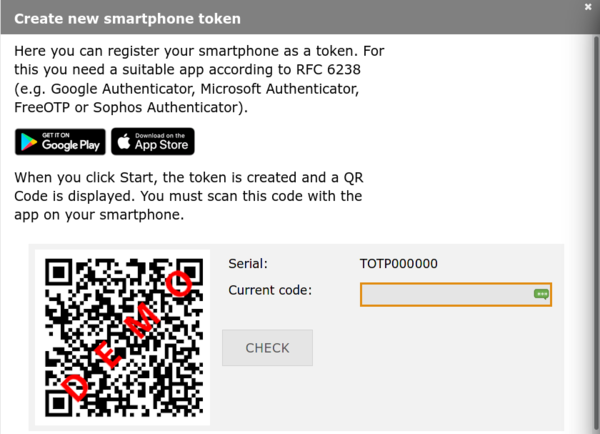
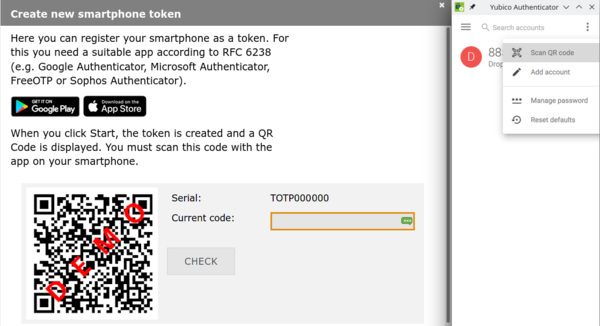
3. A new window opens. Click Start to generate a new QR code. This may take a while.
|
The QR code contains a key which has to remain secret. Only use the QR code to link your software token app with bwIDM/bwServices in the next step. Do not save the QR code, print it out or share it with someone else. |
4. Start the software token app on your separate device and scan the QR code. The exact process is a little bit different in every app, but is usually started by pressing on a button with a plus (+) sign or an icon of a QR code.
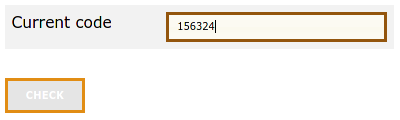
5. Once the QR code has been loaded into your Software Token app there should be a new entry called bwIDM (bwUniCluster, JUSTUS 2 and NEMO2) or bwServices (Helix). Generate an One-Time-Password by pressing on this entry or selecting the appropriate button/menu item. You will receive a six-digit code. Enter this code into the field labeled "Current code:" in your bwIDM browser window to prove that the connection has worked and then click CHECK.
|
If you do not confirm the token by entering the six-digit code in the "Current code:" field, the token will NOT be initialized! |
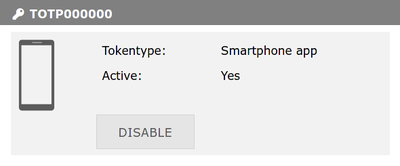
6. If everything worked as expected, you will be returned to the My Tokens screen and there will be a new entry for your software token.
7. Repeat the process to register additional tokens. Please register at least the "Backup TAN list" in addition to the hardware/software token you plan to use regularly.
Registering a new Yubikey OTP Token
|
Please disable all privacy tools, ad blockers and further add-ons when registering new tokens. |
Yubikey OTP is even easier and you don't need a device that displays the six-digit code or extra software. New Yubikeys are already configured to provide Yubikey OTP in slot 1. If you need to configure your Yubikey, read this documentation.
1. Select the registration server of the cluster for which you want to create a second factor and login to it.
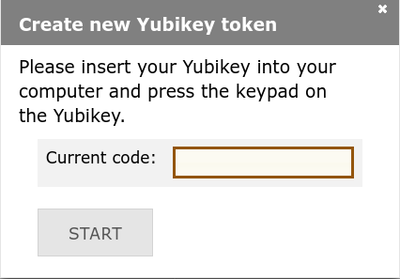
2. If you want to use Yubico OTP, you can click NEW YUBIKEY TOKEN instead.
3. Yubikey OTP is configured to slot 1 on new Yubikeys, so you only need to click in the text box and then touch the metal part of your Yubikey. Please refer to this documentation on how to configure your Yubikey.
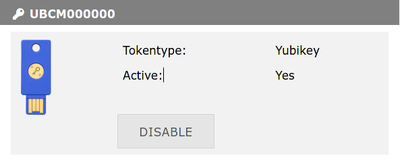
4. If everything worked as expected, you will be returned to the My Tokens screen and there will be a new entry for your Yubikey.
5. Repeat the process to register additional tokens. Please register at least the "Backup TAN list" in addition to the hardware/software token you plan to use regularly.
Registering a new Yubikey OATH TOTP Token
|
Please disable all privacy tools, ad blockers and further add-ons when registering new tokens. |
Yubikey OATH TOTP generates the TANs on your Yubikey and therefore you can use different computers and phones to generate these codes. Please download and install Yubico Authenticator for desktop (or Android/iOS) first. Insert your Yubikey in your computer. "Yubikey OTP" (not "Yubikey OATH TOTP") is even easier and you don't need a device that displays the six-digit code or extra software (go to step Yubikey OTP).
1. Select the registration server of the cluster for which you want to create a second factor and login to it.
2. Registering a new Token starts with a click NEW SMARTPHONE TOKEN.
3. A new window opens. Click Start to generate a new QR code. This may take a while.
|
The QR code contains a key which has to remain secret. Only use the QR code to link your software token app with bwIDM/bwServices in the next step. Do not save the QR code, print it out or share it with someone else. |
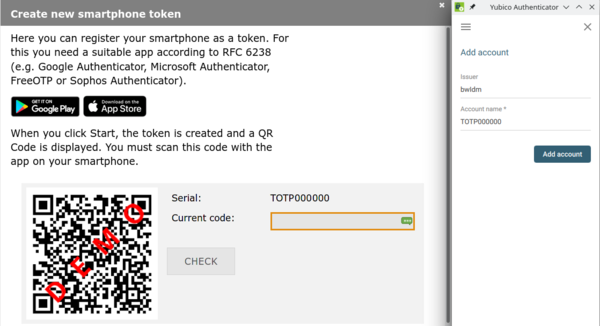
4. Start the Yubico Authenticator on your OS, click the three vertical dots in the upper right corner and select Scan QR code.
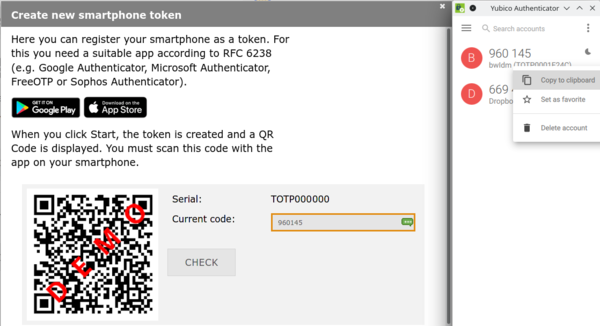
5. Yubico Authenticator automatically translates the QR code to a new entry called bwIDM or bwServices (Helix). Click Add account.
6. You will receive a six-digit code. Enter this code into the field labeled "Current code:" in your bwIDM browser window to prove that the connection has worked and then click CHECK.
7. If everything worked as expected, you will be returned to the My Tokens screen and there will be a new entry for your software token.
8. Repeat the process to register additional tokens. Please register at least the "Backup TAN list" in addition to the hardware/software token you plan to use regularly.
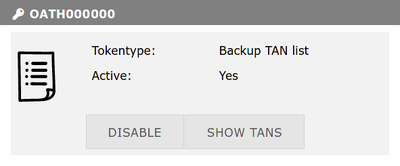
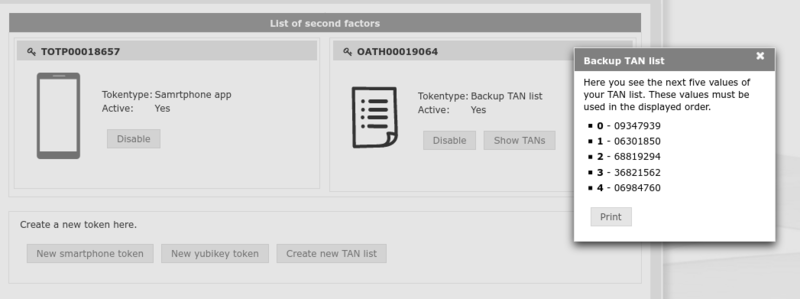
Backup TAN List
|
Passwords from the "Backup TAN list" should only be used if no other token is left. Please do not use the Backup TANs for regular cluster login, because you have only a limited number of TANs. Each TAN can only be used once. Please disable all privacy tools, ad blockers and further add-ons when registering a new Backup TAN list. |
1. Select the registration server of the cluster for which you want to create a second factor and login to it.
2. Please create at least one "Backup TAN list" by clicking CREATE NEW TAN LIST.
3. Click START. You will be redirected to the My Tokens screen and there will be a new entry for your backup TANs.
4. Click SHOW TANS, print the codes and keep then in a separate place for emergencies.
5. Repeat the process to register additional tokens.
Deactivating a Token
Click Disable next to the Token entry on the My Tokens screen.
Deleting a Token
After a Token has been disabled a new button labeled Delete will appear. Click on it to delete the token.
Returning Users
Returning users who have already activated one or more tokens must first verify their token before they can create new tokens or deactivate/delete old ones. If you no longer have valid tokens, you will not be able to create or manage tokens. In this case, read the section Lost Token.
Lost Token
If you change your phone, please migrate your tokens first or register your new mobile app under "My Tokens".
If you no longer have valid tokens (mobile app, hardware token, Yubikey or backup TAN, i.e. lost or broken smartphone), you can not access the section "My Tokens" anymore. In this case you will need to contact the ticket system. Open a ticket, include your user name, the name of the bwHPC cluster and ask for a reset of your 2FA tokens. Please note that this process may take some time and also means additional work for the operators.