Registration/SSH: Difference between revisions
mNo edit summary |
|||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= SSH Key Authentication for HPC Clusters = |
|||
= Registering SSH Keys with your Cluster = |
|||
'''SSH Keys''' allow you to log into a system without entering a password. Instead of proving your identity with something you know (a password), you prove it with something you have (a cryptographic key). |
|||
{| class="wikitable" style="text-align:center;" |
{| class="wikitable" style="text-align:center;" |
||
|+ SSH Key Management |
|+ SSH Key Management Methods by Cluster |
||
|- |
|- |
||
! Cluster |
! Cluster |
||
! Management Method |
|||
! SSH Key Management |
|||
! Details |
|||
|- |
|- |
||
| bwUniCluster 3.0 |
| bwUniCluster 3.0 |
||
| style="background-color:#90EE90;" | |
| style="background-color:#90EE90;" | bwIDM Portal |
||
| Centralized key management, 180-day validity |
|||
|- |
|- |
||
| bwForCluster BinAC 2 |
| bwForCluster BinAC 2 |
||
| style="background-color:# |
| style="background-color:#FFE4B5;" | ~/.ssh/authorized_keys |
||
| Self-managed, use ssh-copy-id |
|||
|- |
|- |
||
| bwForCluster Helix |
| bwForCluster Helix |
||
| style="background-color:#90EE90;" | |
| style="background-color:#90EE90;" | bwServices Portal |
||
| Centralized key management, 180-day validity |
|||
|- |
|- |
||
| bwForCluster JUSTUS 2 |
| bwForCluster JUSTUS 2 |
||
| style="background-color:# |
| style="background-color:#FFE4B5;" | ~/.ssh/authorized_keys |
||
| Self-managed, use ssh-copy-id |
|||
|- |
|- |
||
| bwForCluster NEMO 2 |
| bwForCluster NEMO 2 |
||
| style="background-color:#90EE90;" | |
| style="background-color:#90EE90;" | bwIDM Portal |
||
| Centralized key management, 180-day validity |
|||
|} |
|} |
||
'''Choose your cluster below:''' |
|||
'''Note:''' This guide is only for clusters that use centralized SSH key management through bwIDM/bwServices. |
|||
* [[#SSH_Keys_on_BinAC_2_and_JUSTUS_2|BinAC 2 and JUSTUS 2]] - Self-managed keys |
|||
* [[#SSH_Keys_via_bwIDM.2FbwServices|bwUniCluster 3.0, Helix, and NEMO2]] - Centralized management |
|||
= SSH Keys on BinAC 2 and JUSTUS 2 = |
|||
'''SSH Keys''' allow you to log into a system without entering a password. Instead of proving your identity with something you know (a password), you prove it with something you have (a cryptographic key). |
|||
On '''bwForCluster BinAC 2''' and '''bwForCluster JUSTUS 2''', you manage SSH keys yourself using the standard <code>~/.ssh/authorized_keys</code> file. |
|||
== Why SSH Key Management? == |
|||
== Quick Setup with ssh-copy-id == |
|||
On '''bwUniCluster 3.0''', '''bwForCluster Helix''', and '''bwForCluster NEMO 2''', SSH keys must be managed through bwIDM/bwServices for security reasons: |
|||
The easiest method to add your SSH key: |
|||
* '''Security enforcement:''' Ensures keys use strong algorithms and have limited validity (180 days) |
|||
* '''Centralized management:''' All keys can be reviewed and revoked from one location |
|||
* '''Two types available:''' Interactive keys (for manual logins) and Command keys (for automated workflows) |
|||
'''Step 1: Generate an SSH key''' (if you don't have one): |
|||
'''Note:''' Self-managed <code>~/.ssh/authorized_keys</code> files are ignored on these clusters. |
|||
<pre> |
|||
ssh-keygen -t ed25519 -C "your_email@example.com" |
|||
</pre> |
|||
Press Enter to accept the default location, then set a strong passphrase. |
|||
== SSH Key Requirements == |
|||
'''Step 2: Copy your key to the cluster:''' |
|||
=== Supported Algorithms and Key Sizes === |
|||
<pre> |
|||
# For BinAC2: |
|||
ssh-copy-id username@login.binac2.uni-tuebingen.de |
|||
# For JUSTUS2: |
|||
* '''RSA:''' 2048 bits or more |
|||
ssh-copy-id username@justus2.uni-ulm.de |
|||
* '''ECDSA:''' 521 bits |
|||
</pre> |
|||
* '''ED25519:''' 256 bits (default, recommended) |
|||
* '''ED25519-SK:''' FIDO2 hardware keys (Yubikey, etc.) |
|||
Enter your service password and OTP when prompted. Your public key will be automatically added to <code>~/.ssh/authorized_keys</code>. |
|||
'''Note:''' ECDSA-SK keys are not supported. |
|||
'''Step 3: Test your connection:''' |
|||
<pre> |
|||
# For BinAC2: |
|||
ssh username@login.binac2.uni-tuebingen.de |
|||
# For JUSTUS2: |
|||
ssh username@justus2.uni-ulm.de |
|||
</pre> |
|||
You should now be able to log in using your SSH key and OTP. |
|||
== Manual Setup (Alternative) == |
|||
If <code>ssh-copy-id</code> is not available on your system: |
|||
'''Step 1: Display your public key:''' |
|||
<pre> |
|||
cat ~/.ssh/id_ed25519.pub |
|||
</pre> |
|||
Copy the entire output. |
|||
'''Step 2: Log into the cluster''' using your service password and OTP |
|||
'''Step 3: Add the key to authorized_keys:''' |
|||
<pre> |
|||
mkdir -p ~/.ssh |
|||
chmod 700 ~/.ssh |
|||
echo "paste-your-public-key-here" >> ~/.ssh/authorized_keys |
|||
chmod 600 ~/.ssh/authorized_keys |
|||
</pre> |
|||
Replace <code>paste-your-public-key-here</code> with your actual public key. |
|||
= SSH Keys via bwIDM/bwServices = |
|||
On '''bwUniCluster 3.0''', '''bwForCluster Helix''', and '''bwForCluster NEMO 2''', SSH keys are managed centrally through the registration service. |
|||
== Why Centralized Management? == |
|||
Centralized SSH key management provides: |
|||
* Security enforcement: Keys must use strong algorithms and have 180-day validity |
|||
* Centralized control: Review and revoke all keys from one location |
|||
* Two key types: Interactive keys (manual logins) and Command keys (automated workflows) |
|||
'''Note:''' Self-managed <code>~/.ssh/authorized_keys</code> files are ignored on these clusters. |
|||
== Supported Key Types == |
|||
=== Standard SSH Keys === |
|||
* ED25519: 256 bits (recommended) |
|||
* RSA: 2048 bits or more |
|||
* ECDSA: 521 bits |
|||
'''Important:''' Always protect your private keys with a strong passphrase. |
'''Important:''' Always protect your private keys with a strong passphrase. |
||
=== FIDO2 Hardware Keys |
=== FIDO2 Hardware Keys === |
||
'''ED25519-SK''' keys use hardware security keys (like Yubikey) for authentication: |
|||
{|style="background:#deffee; width:100%;" |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
'''FIDO2 SSH Keys (ED25519-SK)''' offer the best security: |
|||
* |
* Always valid - no 2-factor unlock required |
||
* |
* Hardware-protected - private key never leaves the device |
||
* |
* Physical presence required - must touch key to authenticate |
||
'''Note:''' ECDSA-SK keys are not supported. Use ED25519-SK only. |
|||
See [[Registration/SSH/Yubikey-Quick-Start|SSH with Yubikey - Quick Start Guide]] for setup instructions. |
|||
|} |
|||
{| class="wikitable" style="text-align:center;" |
{| class="wikitable" style="text-align:center;" |
||
|+ FIDO2 |
|+ FIDO2 Key Support by Cluster |
||
|- |
|- |
||
! Cluster |
! Cluster |
||
! |
! ED25519-SK Support |
||
|- |
|- |
||
| bwUniCluster 3.0 |
| bwUniCluster 3.0 |
||
| style="background-color:#90EE90;" | ✓ Supported |
| style="background-color:#90EE90;" | ✓ Supported |
||
|- |
|||
| bwForCluster BinAC 2 |
|||
| style="background-color:#FFB6C1;" | ✗ Not supported |
|||
|- |
|- |
||
| bwForCluster Helix |
| bwForCluster Helix |
||
| style="background-color:#FFB6C1;" | ✗ Not supported |
|||
|- |
|||
| bwForCluster JUSTUS 2 |
|||
| style="background-color:#FFB6C1;" | ✗ Not supported |
| style="background-color:#FFB6C1;" | ✗ Not supported |
||
|- |
|- |
||
| Line 87: | Line 145: | ||
|} |
|} |
||
'''Get started:''' See [[Registration/SSH/SSH-FIDO2-Quick-Start|SSH with FIDO2 - Quick Start Guide]] |
|||
= Adding a new SSH Key = |
|||
== Step 1: Add Your SSH Key to the Portal == |
|||
{|style="background:#deffee; width:100%;" |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
* '''Validity:''' 180 days - keys are automatically revoked after expiration |
|||
* '''Upload:''' Only the '''public key''' file ending in <code>.pub</code> (e.g., <code>~/.ssh/id_ed25519.pub</code>) |
|||
|} |
|||
First, upload your public key to the management portal: |
|||
SSH keys are managed via the '''My SSH Pubkeys''' menu on your cluster's registration page: |
|||
<div style="border: 3px solid #ffc107; padding: 15px; background-color: #fff3cd; margin: 10px 0;"> |
|||
'''1. Navigate to your cluster's SSH key management:''' |
|||
'''Important:''' |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwUniCluster 3.0'''] |
|||
* Keys are valid for '''180 days''' and automatically revoked after expiration |
|||
* [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml '''bwForCluster Helix'''] |
|||
* Upload only your '''public key''' file (ending in <code>.pub</code>, e.g., <code>~/.ssh/id_ed25519.pub</code>) |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwForCluster NEMO 2'''] |
|||
</div> |
|||
'''1. Navigate to SSH key management:''' |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml bwUniCluster 3.0 / NEMO 2] (bwIDM) |
|||
* [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml bwForCluster Helix] (bwServices) |
|||
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys page]] |
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys page]] |
||
'''2. Click |
'''2. Click "Add SSH Key" / "SSH Key Hochladen"''' |
||
[[File:Bwunicluster 2.0 access ssh keys empty.png|center|400px|thumb|Add SSH Key button]] |
[[File:Bwunicluster 2.0 access ssh keys empty.png|center|400px|thumb|Add SSH Key button]] |
||
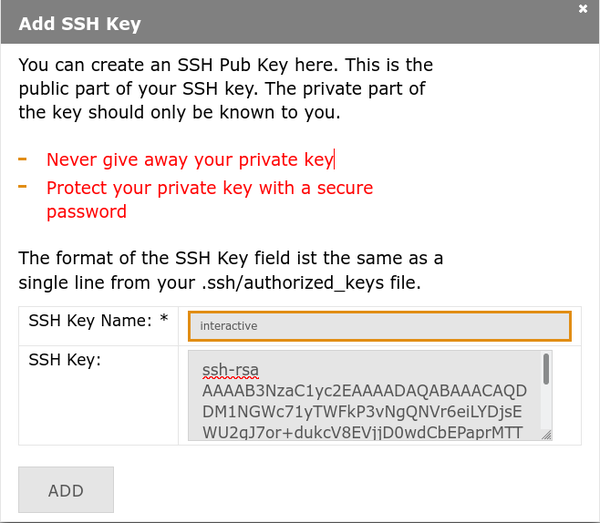
'''3. Enter key details:''' |
'''3. Enter key details:''' |
||
* '''Name:''' Descriptive |
* '''Name:''' Descriptive identifier (e.g., "laptop-work", "desktop-home") |
||
* '''SSH Key:''' Paste |
* '''SSH Key:''' Paste complete contents of your <code>.pub</code> file |
||
* Click '''Add''' / '''Hinzufügen''' |
* Click '''Add''' / '''Hinzufügen''' |
||
[[File:Ssh-key.png|center|600px|thumb|Add SSH key dialog]] |
[[File:Ssh-key.png|center|600px|thumb|Add SSH key dialog]] |
||
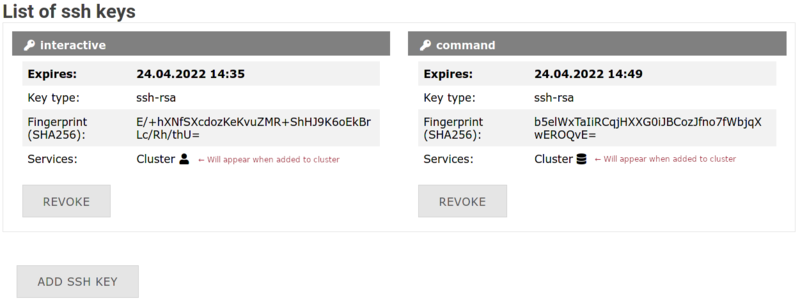
'''4. |
'''4. Success!''' Your key appears in the list |
||
[[File:Ssh-success.png|center|800px|thumb|SSH key successfully added]] |
[[File:Ssh-success.png|center|800px|thumb|SSH key successfully added]] |
||
'''Next:''' Bind your key to a cluster as either an [[#Step_2A:_Register_Interactive_Key|Interactive Key]] or [[#Step_2B:_Register_Command_Key|Command Key]]. |
|||
== Step 2A: Register Interactive Key == |
|||
'''Next step:''' Bind your key to a service as either an '''Interactive Key''' (manual logins) or '''Command Key''' (automated workflows). |
|||
'''Interactive Keys''' are for manual SSH logins. |
|||
=== Understanding Key Validity === |
|||
== Registering an Interactive Key == |
|||
'''Regular SSH Keys''' (RSA, ECDSA, ED25519): |
|||
'''Interactive Keys''' are used for manual SSH logins to work on the cluster. |
|||
* Require 2-factor authentication unlock |
|||
* Valid for limited hours after entering OTP + service password |
|||
=== Key Validity and 2-Factor Authentication === |
|||
* Must re-authenticate when validity expires |
|||
{|style="background:#deffee; width:100%;" |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
'''Regular SSH Keys''' require 2-factor unlock: |
|||
* Keys are only valid for limited hours after entering OTP and service password |
|||
* Must re-authenticate after validity expires |
|||
'''FIDO2 SSH Keys (ED25519-SK)''' work differently: |
|||
* '''Always valid''' - no 2-factor unlock needed |
|||
* Authentication via physical key touch only |
|||
* Recommended for best security and convenience |
|||
* '''Available on: bwUniCluster 3.0 and NEMO 2 only''' (not on Helix) |
|||
|} |
|||
{| class="wikitable" style="text-align:center;" |
{| class="wikitable" style="text-align:center;" |
||
|+ Validity |
|+ Validity Periods for Regular SSH Keys |
||
|- |
|- |
||
! Cluster |
! Cluster |
||
! Valid Duration |
|||
! Validity after 2FA Login |
|||
|- |
|- |
||
| bwUniCluster 3.0 |
| bwUniCluster 3.0 |
||
| Line 159: | Line 204: | ||
| bwForCluster NEMO 2 |
| bwForCluster NEMO 2 |
||
| 12 hours |
| 12 hours |
||
|- |
|||
|} |
|} |
||
'''FIDO2 Hardware Keys''' (ED25519-SK): |
|||
* Always valid - no 2-factor unlock needed |
|||
* Authentication via physical key touch only |
|||
* Only on bwUniCluster 3.0 and NEMO 2 (not Helix) |
|||
* See [[Registration/SSH/SSH-FIDO2-Quick-Start|SSH with FIDO2 - Quick Start Guide]] |
|||
=== Registration Steps === |
=== Registration Steps === |
||
'''1. Add your public key''' following [[#Step_1:_Add_Your_SSH_Key_to_the_Portal|Step 1]] above |
|||
'''1.''' [[Registration/SSH#Adding_a_new_SSH_Key|Add your SSH key]] if not already done |
|||
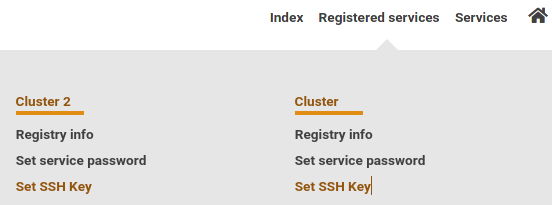
'''2. |
'''2. Navigate to "Registered Services" / "Registrierte Dienste"''' |
||
Click '''Set SSH Key''' / '''SSH Key setzen''' for your cluster |
|||
[[File:BwIDM-registered.png|center|600px|thumb|Select cluster]] |
[[File:BwIDM-registered.png|center|600px|thumb|Select cluster]] |
||
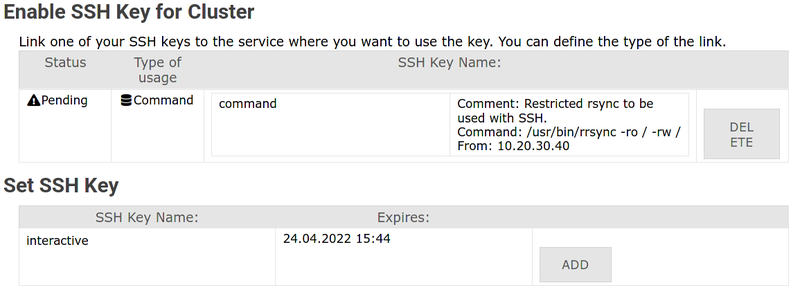
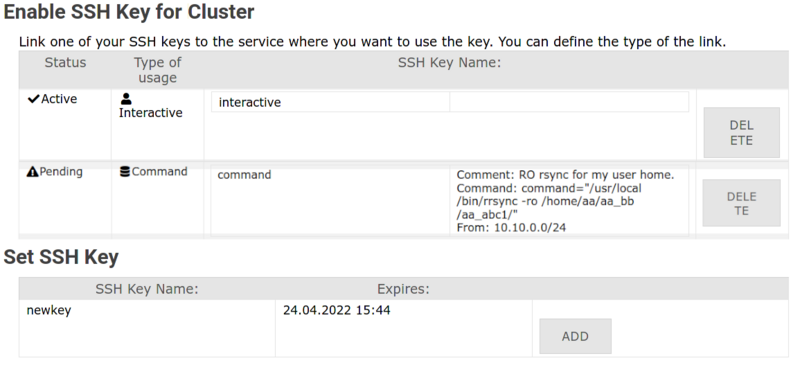
'''3. |
'''3. Find your key and click "Add" / "Hinzufügen"''' |
||
[[File:Ssh-service-int.png|center|800px|thumb|Add SSH key to service]] |
[[File:Ssh-service-int.png|center|800px|thumb|Add SSH key to service]] |
||
'''4. |
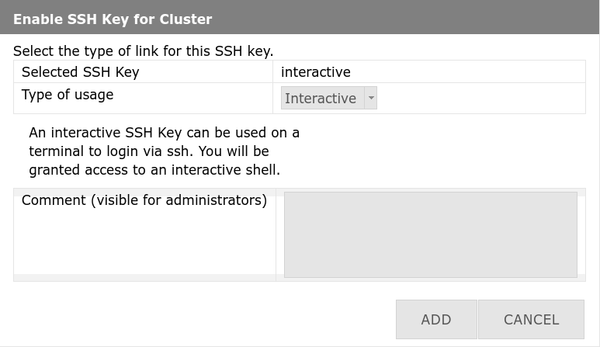
'''4. Select "Interactive" and confirm''' |
||
* Usage type: '''Interactive''' |
|||
* Comment: Optional description |
|||
* Click '''Add''' / '''Hinzufügen''' |
|||
[[File:Ssh-int.png|center|600px|thumb|Set as Interactive key]] |
[[File:Ssh-int.png|center|600px|thumb|Set as Interactive key]] |
||
'''5.''' |
'''5. Done!''' Your key is active for interactive logins |
||
[[File:Ssh-service.png|center|800px|thumb|SSH key registered]] |
[[File:Ssh-service.png|center|800px|thumb|SSH key registered]] |
||
== |
== Step 2B: Register Command Key == |
||
'''Command Keys''' enable automated workflows |
'''Command Keys''' enable automated workflows (e.g., backups, data transfers) without manual login. |
||
=== Security Requirements === |
=== Security Requirements === |
||
<div style="border: 3px solid #dc3545; padding: 15px; background-color: #f8d7da; margin: 10px 0;"> |
|||
Command keys are '''always valid''' (no 2FA required), making them security-sensitive. |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
Command keys are '''always valid''' (no 2FA required), making them high-value targets. |
|||
'''Mandatory restrictions:''' |
'''Mandatory restrictions:''' |
||
* |
* Single command: Specify exact command with full path |
||
* |
* IP restriction: Limit to specific IP address(es) or subnet |
||
* |
* Admin approval: Keys require review before activation |
||
* |
* Short validity: Maximum 30 days |
||
</div> |
|||
|} |
|||
'''Common use case:''' |
'''Common use case:''' [[Registration/SSH/rrsync|rrsync for data transfers]] |
||
=== Registration Steps === |
=== Registration Steps === |
||
'''1. Add your public key''' following [[#Step_1:_Add_Your_SSH_Key_to_the_Portal|Step 1]] above |
|||
'''1.''' [[Registration/SSH#Adding_a_new_SSH_Key|Add your SSH key]] if not already done |
|||
'''2. |
'''2. Navigate to "Registered Services"''' |
||
Click '''Set SSH Key''' for your cluster |
|||
[[File:BwIDM-registered.png|center|600px|thumb|Select cluster]] |
[[File:BwIDM-registered.png|center|600px|thumb|Select cluster]] |
||
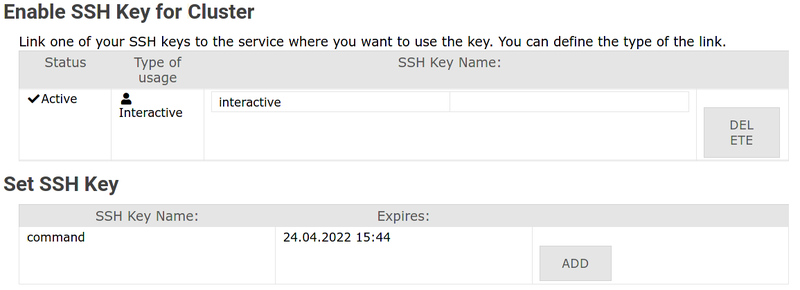
'''3. |
'''3. Find your key and click "Add" / "Hinzufügen"''' |
||
[[File:Ssh-service-com.png|center|800px|thumb|Add SSH key to service]] |
[[File:Ssh-service-com.png|center|800px|thumb|Add SSH key to service]] |
||
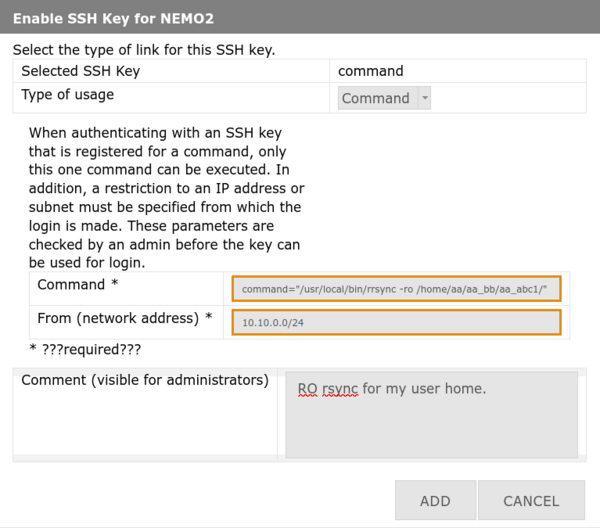
'''4. |
'''4. Configure command restrictions:''' |
||
* '''Usage type:''' Select '''Command''' |
* '''Usage type:''' Select '''Command''' |
||
* '''Command:''' |
* '''Command:''' Full path with parameters (see example below) |
||
* '''From:''' |
* '''From:''' IP address or CIDR notation (e.g., <code>192.168.1.0/24</code>) |
||
* '''Comment:''' Explain purpose (speeds up approval) |
* '''Comment:''' Explain purpose (speeds up approval) |
||
* Click '''Add''' / '''Hinzufügen''' |
* Click '''Add''' / '''Hinzufügen''' |
||
{| class="wikitable" |
{| class="wikitable" |
||
! Example: rrsync for |
! Example: rrsync for data transfer |
||
|- |
|- |
||
| <pre>/usr/local/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/</pre> |
| <pre>/usr/local/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/</pre> |
||
Note: Verify |
'''Note:''' Verify exact path on your cluster (may be <code>/usr/bin/rrsync</code>) |
||
|} |
|} |
||
[[File:Ssh-com.png|center|600px|thumb|Configure command key]] |
[[File:Ssh-com.png|center|600px|thumb|Configure command key]] |
||
'''5. |
'''5. Wait for approval''' |
||
[[File:Ssh-service.png|center|800px|thumb|Key pending approval]] |
[[File:Ssh-service.png|center|800px|thumb|Key pending approval]] |
||
You'll receive an email when the key is approved and ready to use. |
|||
== Revoking SSH Keys == |
== Revoking SSH Keys == |
||
Revoke keys that are no longer needed or potentially compromised. |
|||
Revoked keys are immediately disabled and cannot be reused. |
|||
<div style="border: 3px solid #6c757d; padding: 15px; background-color: #e2e3e5; margin: 10px 0;"> |
|||
'''1.''' Navigate to your cluster's SSH key management: |
|||
'''Note:''' Revoked keys are immediately disabled and cannot be reused. |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwUniCluster 3.0'''] |
|||
</div> |
|||
* [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml '''bwForCluster Helix'''] |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwForCluster NEMO 2'''] |
|||
'''1. Navigate to SSH key management:''' |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml bwUniCluster 3.0 / NEMO 2] (bwIDM) |
|||
* [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml bwForCluster Helix] (bwServices) |
|||
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys page]] |
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys page]] |
||
'''2. Click "REVOKE" / "ZURÜCKZIEHEN"''' next to the key you want to disable |
|||
'''2.''' Click '''REVOKE''' / '''ZURÜCKZIEHEN''' next to the key you want to disable |
'''2.''' Click '''REVOKE''' / '''ZURÜCKZIEHEN''' next to the key you want to disable |
||
Latest revision as of 15:27, 12 January 2026
SSH Key Authentication for HPC Clusters
SSH Keys allow you to log into a system without entering a password. Instead of proving your identity with something you know (a password), you prove it with something you have (a cryptographic key).
| Cluster | Management Method | Details |
|---|---|---|
| bwUniCluster 3.0 | bwIDM Portal | Centralized key management, 180-day validity |
| bwForCluster BinAC 2 | ~/.ssh/authorized_keys | Self-managed, use ssh-copy-id |
| bwForCluster Helix | bwServices Portal | Centralized key management, 180-day validity |
| bwForCluster JUSTUS 2 | ~/.ssh/authorized_keys | Self-managed, use ssh-copy-id |
| bwForCluster NEMO 2 | bwIDM Portal | Centralized key management, 180-day validity |
Choose your cluster below:
- BinAC 2 and JUSTUS 2 - Self-managed keys
- bwUniCluster 3.0, Helix, and NEMO2 - Centralized management
SSH Keys on BinAC 2 and JUSTUS 2
On bwForCluster BinAC 2 and bwForCluster JUSTUS 2, you manage SSH keys yourself using the standard ~/.ssh/authorized_keys file.
Quick Setup with ssh-copy-id
The easiest method to add your SSH key:
Step 1: Generate an SSH key (if you don't have one):
ssh-keygen -t ed25519 -C "your_email@example.com"
Press Enter to accept the default location, then set a strong passphrase.
Step 2: Copy your key to the cluster:
# For BinAC2: ssh-copy-id username@login.binac2.uni-tuebingen.de # For JUSTUS2: ssh-copy-id username@justus2.uni-ulm.de
Enter your service password and OTP when prompted. Your public key will be automatically added to ~/.ssh/authorized_keys.
Step 3: Test your connection:
# For BinAC2: ssh username@login.binac2.uni-tuebingen.de # For JUSTUS2: ssh username@justus2.uni-ulm.de
You should now be able to log in using your SSH key and OTP.
Manual Setup (Alternative)
If ssh-copy-id is not available on your system:
Step 1: Display your public key:
cat ~/.ssh/id_ed25519.pub
Copy the entire output.
Step 2: Log into the cluster using your service password and OTP
Step 3: Add the key to authorized_keys:
mkdir -p ~/.ssh chmod 700 ~/.ssh echo "paste-your-public-key-here" >> ~/.ssh/authorized_keys chmod 600 ~/.ssh/authorized_keys
Replace paste-your-public-key-here with your actual public key.
SSH Keys via bwIDM/bwServices
On bwUniCluster 3.0, bwForCluster Helix, and bwForCluster NEMO 2, SSH keys are managed centrally through the registration service.
Why Centralized Management?
Centralized SSH key management provides:
- Security enforcement: Keys must use strong algorithms and have 180-day validity
- Centralized control: Review and revoke all keys from one location
- Two key types: Interactive keys (manual logins) and Command keys (automated workflows)
Note: Self-managed ~/.ssh/authorized_keys files are ignored on these clusters.
Supported Key Types
Standard SSH Keys
- ED25519: 256 bits (recommended)
- RSA: 2048 bits or more
- ECDSA: 521 bits
Important: Always protect your private keys with a strong passphrase.
FIDO2 Hardware Keys
ED25519-SK keys use hardware security keys (like Yubikey) for authentication:
- Always valid - no 2-factor unlock required
- Hardware-protected - private key never leaves the device
- Physical presence required - must touch key to authenticate
Note: ECDSA-SK keys are not supported. Use ED25519-SK only.
| Cluster | ED25519-SK Support |
|---|---|
| bwUniCluster 3.0 | ✓ Supported |
| bwForCluster Helix | ✗ Not supported |
| bwForCluster NEMO 2 | ✓ Supported |
Get started: See SSH with FIDO2 - Quick Start Guide
Step 1: Add Your SSH Key to the Portal
First, upload your public key to the management portal:
Important:
- Keys are valid for 180 days and automatically revoked after expiration
- Upload only your public key file (ending in
.pub, e.g.,~/.ssh/id_ed25519.pub)
1. Navigate to SSH key management:
- bwUniCluster 3.0 / NEMO 2 (bwIDM)
- bwForCluster Helix (bwServices)
2. Click "Add SSH Key" / "SSH Key Hochladen"
3. Enter key details:
- Name: Descriptive identifier (e.g., "laptop-work", "desktop-home")
- SSH Key: Paste complete contents of your
.pubfile - Click Add / Hinzufügen
4. Success! Your key appears in the list
Next: Bind your key to a cluster as either an Interactive Key or Command Key.
Step 2A: Register Interactive Key
Interactive Keys are for manual SSH logins.
Understanding Key Validity
Regular SSH Keys (RSA, ECDSA, ED25519):
- Require 2-factor authentication unlock
- Valid for limited hours after entering OTP + service password
- Must re-authenticate when validity expires
| Cluster | Valid Duration |
|---|---|
| bwUniCluster 3.0 | 8 hours |
| bwForCluster Helix | 12 hours |
| bwForCluster NEMO 2 | 12 hours |
FIDO2 Hardware Keys (ED25519-SK):
- Always valid - no 2-factor unlock needed
- Authentication via physical key touch only
- Only on bwUniCluster 3.0 and NEMO 2 (not Helix)
- See SSH with FIDO2 - Quick Start Guide
Registration Steps
1. Add your public key following Step 1 above
2. Navigate to "Registered Services" / "Registrierte Dienste"
Click Set SSH Key / SSH Key setzen for your cluster
3. Find your key and click "Add" / "Hinzufügen"
4. Select "Interactive" and confirm
- Usage type: Interactive
- Comment: Optional description
- Click Add / Hinzufügen
5. Done! Your key is active for interactive logins
Step 2B: Register Command Key
Command Keys enable automated workflows (e.g., backups, data transfers) without manual login.
Security Requirements
Command keys are always valid (no 2FA required), making them security-sensitive.
Mandatory restrictions:
- Single command: Specify exact command with full path
- IP restriction: Limit to specific IP address(es) or subnet
- Admin approval: Keys require review before activation
- Short validity: Maximum 30 days
Common use case: rrsync for data transfers
Registration Steps
1. Add your public key following Step 1 above
2. Navigate to "Registered Services"
Click Set SSH Key for your cluster
3. Find your key and click "Add" / "Hinzufügen"
4. Configure command restrictions:
- Usage type: Select Command
- Command: Full path with parameters (see example below)
- From: IP address or CIDR notation (e.g.,
192.168.1.0/24) - Comment: Explain purpose (speeds up approval)
- Click Add / Hinzufügen
| Example: rrsync for data transfer |
|---|
/usr/local/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/ Note: Verify exact path on your cluster (may be |
5. Wait for approval
Revoking SSH Keys
Revoke keys that are no longer needed or potentially compromised.
Note: Revoked keys are immediately disabled and cannot be reused.
1. Navigate to SSH key management:
- bwUniCluster 3.0 / NEMO 2 (bwIDM)
- bwForCluster Helix (bwServices)
2. Click "REVOKE" / "ZURÜCKZIEHEN" next to the key you want to disable
2. Click REVOKE / ZURÜCKZIEHEN next to the key you want to disable