Registration/SSH: Difference between revisions
mNo edit summary |
|||
| Line 1: | Line 1: | ||
{|style="background:# |
{|style="background:#ffe6e6; width:100%; border:2px solid #ff4444;" |
||
|style="padding: |
|style="padding:10px; background:#ffcccc; text-align:center; font-weight:bold; font-size:1.1em;"| |
||
[[Image:Attention.svg|center| |
[[Image:Attention.svg|center|30px]] |
||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
'''This guide applies ONLY to:''' |
|||
This process is only necessary for the bwUniCluster and the bwForCluster Helix and NEMO2. |
|||
On the other clusters, SSH keys can still be copied to the <code>authorized_keys</code> file. |
|||
'''bwUniCluster 3.0''' • '''bwForCluster Helix''' • '''bwForCluster NEMO 2''' |
|||
On all other clusters, SSH keys are still managed via <code>~/.ssh/authorized_keys</code> files. |
|||
|} |
|} |
||
| Line 10: | Line 13: | ||
= Registering SSH Keys with your Cluster = |
= Registering SSH Keys with your Cluster = |
||
'''SSH Keys''' allow you to log into a system without entering a password. Instead of proving your identity with something you know (a password), you prove it with something you have (a cryptographic key). |
|||
{|style="background:#deffee; width:100%;" |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
Interactive SSH Keys are not valid all the time, but only for a few hours after the last 2-factor login. |
|||
They have to be "unlocked" by entering the OTP and service password. |
|||
|} |
|||
== Why SSH Key Management? == |
|||
'''SSH Keys''' are a mechanism for logging into a computer system without having to enter a password. Instead of authenticating yourself with something you know (a password), you prove your identity by showing the server something you have (a cryptographic key). |
|||
On '''bwUniCluster 3.0''', '''bwForCluster Helix''', and '''bwForCluster NEMO 2''', SSH keys must be managed through bwIDM/bwServices for security reasons: |
|||
The usual process is the following: |
|||
* '''Security enforcement:''' Ensures keys use strong algorithms and have limited validity (180 days) |
|||
* The user generates a pair of SSH Keys, a private key and a public key, on their local system. The private key never leaves the local system. |
|||
* '''Centralized management:''' All keys can be reviewed and revoked from one location |
|||
* '''Two types available:''' Interactive keys (for manual logins) and Command keys (for automated workflows) |
|||
'''Note:''' Self-managed <code>~/.ssh/authorized_keys</code> files are ignored on these clusters. |
|||
* The user then logs into the remote system using the remote system password and adds the public key to a file called ~/.ssh/authorized_keys . |
|||
== SSH Key Requirements == |
|||
* All following logins will no longer require the entry of the remote system password because the local system can prove to the remote system that it has a private key matching the public key on file. |
|||
=== Supported Algorithms and Key Sizes === |
|||
While SSH Keys have many advantages, the concept also has '''a number of issues''' which make it hard to handle them securely: |
|||
* '''RSA:''' 2048 bits or more |
|||
* The private key on the local system is supposed to be protected by a strong passphrase. There is no possibility for the server to check if this is the case. Many users do not use a strong passphrase or do not use any passphrase at all. If such a private key is stolen, an attacker can immediately use it to access the remote system. |
|||
* '''ECDSA:''' 521 bits |
|||
* '''ED25519:''' 256 bits (default, recommended) |
|||
* '''ECDSA-SK / ED25519-SK:''' FIDO2 hardware keys (Yubikey, etc.) |
|||
'''Important:''' Always protect your private keys with a strong passphrase. |
|||
* There is no concept of validity. Users are not forced to regularly generate new SSH Key pairs and replace the old ones. Often the same key pair is used for many years and the users have no overview of how many systems they have stored their SSH Keys on. |
|||
=== FIDO2 Hardware Keys (Recommended) === |
|||
* SSH Keys can be restricted so they can only be used to execute specific commands on the server, or to log in from specified IP addresses. Most users do not do this. |
|||
{|style="background:#deffee; width:100%;" |
|||
To fix these issues '''it is no longer possible to self-manage your SSH Keys by adding them to the ~/.ssh/authorized_keys file''' on bwUniCluster/bwForCluster. |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
SSH Keys have to be managed through bwIDM/bwServces instead. |
|||
[[Image:Attention.svg|center|25px]] |
|||
Existing authorized_keys files are ignored. |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
'''FIDO2 SSH Keys (ECDSA-SK and ED25519-SK)''' offer the best security: |
|||
* '''Always valid''' - no 2-factor unlock required |
|||
== Minimum requirements for SSH Keys == |
|||
* '''Hardware-protected''' - private key never leaves the device |
|||
* '''Physical presence required''' - must touch key to authenticate |
|||
See [[Registration/SSH/Yubikey-Quick-Start|SSH with Yubikey - Quick Start Guide]] for setup instructions. |
|||
Algorithms and Key sizes: |
|||
|} |
|||
{|style="background:#fff3cd; width:100%; border:2px solid #ff9800;" |
|||
* 2048 bits or more for RSA |
|||
|style="padding:8px; background:#ffe8a1; text-align:center; font-weight:bold;"| |
|||
* 521 bits for ECDSA |
|||
[[Image:Attention.svg|center|25px]] |
|||
* 256 Bits (Default) for ED25519 |
|||
'''FIDO2 SSH Keys currently work ONLY on:''' |
|||
'''Please set a strong passphrase for your private keys.''' |
|||
'''bwUniCluster 3.0''' and '''bwForCluster NEMO 2''' |
|||
ECDSA-SK and ED25519-SK keys (for use with U2F/FIDO Hardware Tokens like Yubikeys) can currently only be used on NEMO2 and bwUniCluster 3.0. |
|||
'''NOT supported on bwForCluster Helix!''' |
|||
|} |
|||
= Adding a new SSH Key = |
= Adding a new SSH Key = |
||
| Line 58: | Line 68: | ||
[[Image:Attention.svg|center|25px]] |
[[Image:Attention.svg|center|25px]] |
||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|style="padding:5px; background:#cef2e0; text-align:left"| |
||
* '''Validity:''' 180 days - keys are automatically revoked after expiration |
|||
* Newly added keys are valid for 180 days. After that, they are revoked and placed on a "revocation list" so that they cannot be reused. |
|||
* |
* '''Upload:''' Only the '''public key''' file ending in <code>.pub</code> (e.g., <code>~/.ssh/id_ed25519.pub</code>) |
||
|} |
|} |
||
SSH keys are managed via the '''My SSH Pubkeys''' menu on your cluster's registration page: |
|||
Here you can add and revoke SSH keys. To add a ssh key, please follow these steps: |
|||
'''1. Navigate to your cluster's SSH key management:''' |
|||
1. '''Select the cluster''' for which you want to create a second factor:</br> → [https://login.bwidm.de/user/ssh-keys.xhtml '''bwUniCluster 3.0''']</br> → [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml '''bwForCluster Helix''']</br> → [https://login.bwidm.de/user/ssh-keys.xhtml '''bwForCluster NEMO 2'''] |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwUniCluster 3.0'''] |
|||
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys.]] |
|||
* [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml '''bwForCluster Helix'''] |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwForCluster NEMO 2'''] |
|||
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys page]] |
|||
3. Click the '''Add SSH Key''' or '''SSH Key Hochladen''' button. |
|||
[[File:Bwunicluster 2.0 access ssh keys empty.png|center|400px|thumb|Add new SSH key.]] |
|||
'''2. Click''' '''Add SSH Key''' / '''SSH Key Hochladen''' |
|||
4. A new window will appear. |
|||
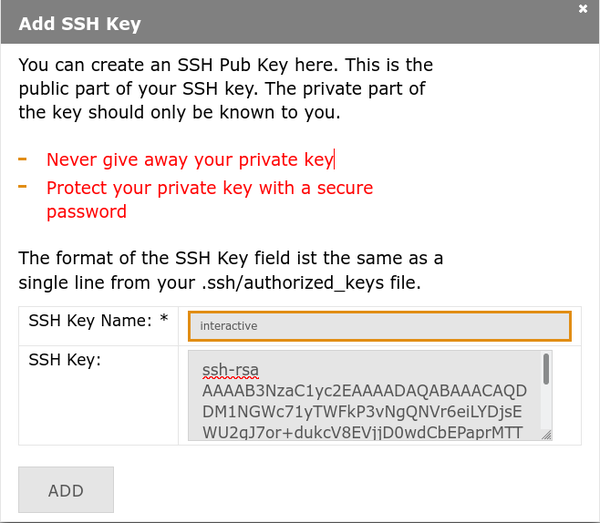
Enter a name for the key and paste your SSH public key (file <code>~/.ssh/<filename>.pub</code>) into the box labelled "SSH Key:". |
|||
Click on the button labelled '''Add''' or '''Hinzufügen'''. |
|||
[[File:Ssh-key.png|center|600px|thumb|Add new SSH key.]] |
|||
[[File:Bwunicluster 2.0 access ssh keys empty.png|center|400px|thumb|Add SSH Key button]] |
|||
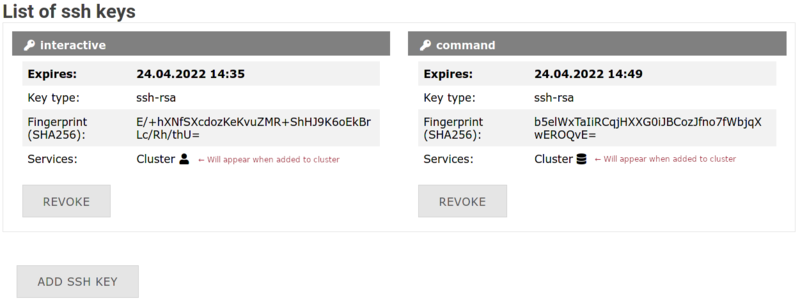
5. If everything worked fine your new key will show up in the user interface: |
|||
[[File:Ssh-success.png|center|800px|thumb|New SSH key added.]] |
|||
'''3. Enter key details:''' |
|||
Once you have added SSH keys to the system, you can bind them to one or more services to use either for interactive logins ('''Interactive key''') or for automatic logins ('''Command key'''). |
|||
* '''Name:''' Descriptive name for your key (e.g., "laptop-work") |
|||
* '''SSH Key:''' Paste the complete contents of your <code>.pub</code> file |
|||
* Click '''Add''' / '''Hinzufügen''' |
|||
[[File:Ssh-key.png|center|600px|thumb|Add SSH key dialog]] |
|||
'''4. Confirmation:''' Your new key appears in the list |
|||
== Registering an Interactive Key == |
|||
[[File:Ssh-success.png|center|800px|thumb|SSH key successfully added]] |
|||
{|style="background:#deffee; width:100%;" |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
Interactive SSH Keys are not valid all the time, but only for a few hours after the last 2-factor login. |
|||
They have to be "unlocked" by entering the OTP and service password. |
|||
|} |
|||
'''Next step:''' Bind your key to a service as either an '''Interactive Key''' (manual logins) or '''Command Key''' (automated workflows). |
|||
'''Interactive Keys''' can be used to log into a system for interactive use. |
|||
Perform the following steps to register an interactive key: |
|||
1. [[Registration/SSH#Adding_a_new_SSH_Key|'''Add a new interactive SSH key''']] if you have not already done so. |
|||
== Registering an Interactive Key == |
|||
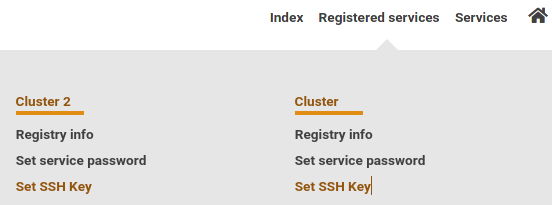
2. Select '''Registered services/Registrierte Dienste''' from the top menu and click '''Set SSH Key/SSH Key setzen''' for the cluster for which you want to use the SSH key. |
|||
[[File:BwIDM-registered.png|center|600px|thumb|Select Cluster for which you want to use the SSH key.]] |
|||
'''Interactive Keys''' are used for manual SSH logins to work on the cluster. |
|||
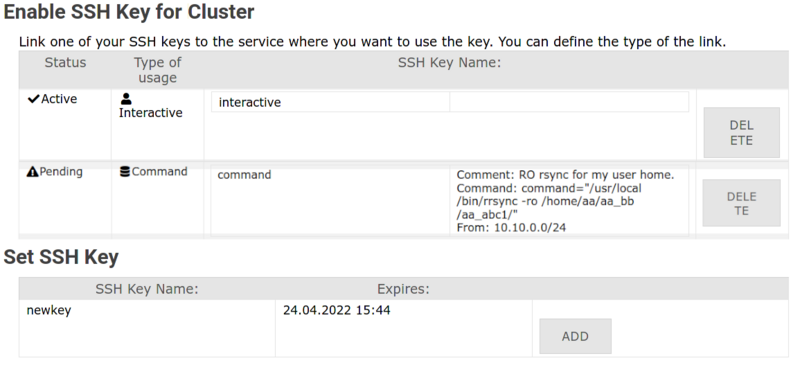
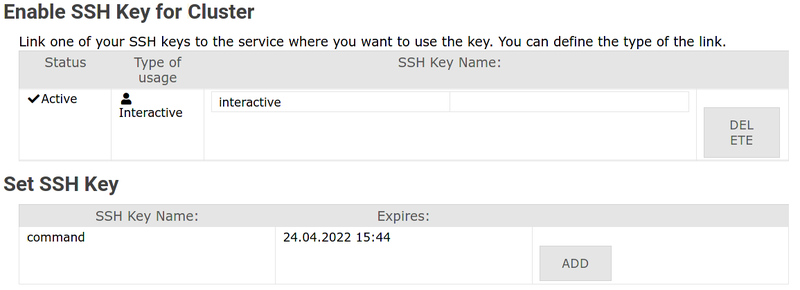
3. The upper block displays the SSH keys currently registered for the service. |
|||
The bottom block displays all the public SSH keys associated with your account. |
|||
Find the SSH key you want to use and click '''Add/Hinzufügen'''. |
|||
[[File:Ssh-service-int.png|center|800px|thumb|Add SSH key to service.]] |
|||
=== Key Validity and 2-Factor Authentication === |
|||
4. A new window appears. |
|||
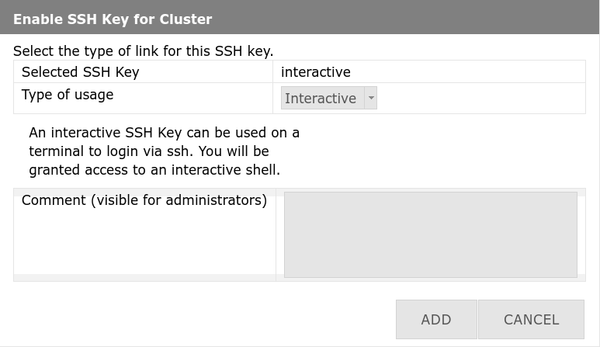
Select '''Interactive''' as the usage type, enter an optional comment and click '''Add/Hinzufügen'''. |
|||
[[File:Ssh-int.png|center|600px|thumb|Add interactive SSH key to service.]] |
|||
{|style="background:#deffee; width:100%;" |
|||
5. Your SSH key is now registered for interactive use with this service. |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
[[File:Ssh-service.png|center|800px|thumb|SSH key is now registered for interactive use.]] |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
'''Regular SSH Keys''' require 2-factor unlock: |
|||
* Keys are only valid for limited hours after entering OTP and service password |
|||
* Must re-authenticate after validity expires |
|||
'''FIDO2 SSH Keys (ECDSA-SK/ED25519-SK)''' work differently: |
|||
=== SSH Interactive Key valid after successful Login === |
|||
* '''Always valid''' - no 2-factor unlock needed |
|||
* Authentication via physical key touch only |
|||
Interactive SSH Keys are not valid all the time, but only for a few hours after the last 2-factor login. |
|||
* Recommended for best security and convenience |
|||
They have to be "unlocked" by entering the OTP and service password. |
|||
* '''Available on: bwUniCluster 3.0 and NEMO 2 only''' (not on Helix) |
|||
|} |
|||
{| class="wikitable" style="text-align:center;" |
{| class="wikitable" style="text-align:center;" |
||
|+ Validity periods for regular SSH keys |
|||
|- |
|- |
||
! |
! Cluster |
||
! Validity after 2FA Login |
|||
! style="width:50%"| Interactive SSH Key Validity |
|||
|- |
|- |
||
| bwUniCluster 3.0 |
|||
| |
| 8 hours |
||
|- |
|- |
||
| bwForCluster Helix |
|||
| 12 hours |
|||
| 12h |
|||
|- |
|- |
||
| bwForCluster NEMO 2 |
|||
| 12 hours |
|||
| 12h |
|||
|- |
|- |
||
|} |
|} |
||
=== Registration Steps === |
|||
'''1.''' [[Registration/SSH#Adding_a_new_SSH_Key|Add your SSH key]] if not already done |
|||
'''2.''' Navigate to '''Registered Services''' / '''Registrierte Dienste''' → Click '''Set SSH Key''' / '''SSH Key setzen''' for your cluster |
|||
[[File:BwIDM-registered.png|center|600px|thumb|Select cluster]] |
|||
'''3.''' Find your key in the bottom section → Click '''Add''' / '''Hinzufügen''' |
|||
[[File:Ssh-service-int.png|center|800px|thumb|Add SSH key to service]] |
|||
'''4.''' Select '''Interactive''' as usage type → Add optional comment → Click '''Add''' / '''Hinzufügen''' |
|||
[[File:Ssh-int.png|center|600px|thumb|Set as Interactive key]] |
|||
'''5.''' Done! Your key is now active for interactive logins |
|||
[[File:Ssh-service.png|center|800px|thumb|SSH key registered]] |
|||
== Registering a Command Key == |
== Registering a Command Key == |
||
'''Command Keys''' enable automated workflows without manual login (e.g., automated backups, data transfers). |
|||
=== Security Requirements === |
|||
{|style="background:#deffee; width:100%;" |
{|style="background:#deffee; width:100%;" |
||
| Line 139: | Line 167: | ||
[[Image:Attention.svg|center|25px]] |
[[Image:Attention.svg|center|25px]] |
||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|style="padding:5px; background:#cef2e0; text-align:left"| |
||
Command keys are '''always valid''' (no 2FA required), making them high-value targets. |
|||
This makes these keys extremely valuable to a potential attacker and poses a security risk. |
|||
'''Mandatory restrictions:''' |
|||
* |
* '''Single command:''' Must specify exact command with full path |
||
* |
* '''IP restriction:''' Limited to specific IP address(es) or subnet |
||
* |
* '''Admin approval:''' Keys must be reviewed before activation |
||
* '''Short validity:''' Maximum 30 days |
|||
* Validity is reduced to one month. |
|||
|} |
|} |
||
'''Common use case:''' For rsync data transfers, see the [[Registration/SSH/rrsync|rrsync wiki guide]]. |
|||
'''Command Keys''' can be used for automatic workflows. |
|||
If you want to use rsync, please read the [[Registration/SSH/rrsync|rrsync wiki]]. |
|||
=== Registration Steps === |
|||
Perform the following steps to register a "Command key" (in this example we use rrsync): |
|||
1. [[Registration/SSH#Adding_a_new_SSH_Key| |
'''1.''' [[Registration/SSH#Adding_a_new_SSH_Key|Add your SSH key]] if not already done |
||
'''2.''' Navigate to '''Registered Services''' → Click '''Set SSH Key''' for your cluster |
|||
[[File:BwIDM-registered.png|center|600px|thumb|Select cluster]] |
|||
2. Select '''Registered services/Registrierte Dienste''' from the top menu and click '''Set SSH Key/SSH Key setzen''' for the cluster for which you want to use the SSH key. |
|||
[[File:BwIDM-registered.png|center|600px|thumb|Select Cluster for which you want to use the SSH key.]] |
|||
'''3.''' Find your key in the bottom section → Click '''Add''' / '''Hinzufügen''' |
|||
3. The upper block displays the SSH keys currently registered for the service. |
|||
The bottom block displays all the public SSH keys associated with your account. |
|||
[[File:Ssh-service-com.png|center|800px|thumb|Add SSH key to service]] |
|||
Find the SSH key you want to use and click '''Add/Hinzufügen'''. |
|||
[[File:Ssh-service-com.png|center|800px|thumb|Add SSH key to service.]] |
|||
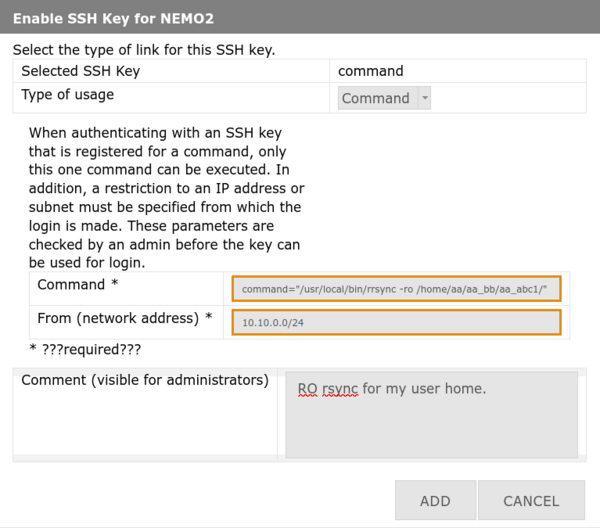
'''4.''' Configure command restrictions: |
|||
* '''Usage type:''' Select '''Command''' |
|||
* '''Command:''' Enter full path and parameters (example for rrsync below) |
|||
* '''From:''' Specify IP address, range, or subnet (see [https://man.openbsd.org/sshd.8#from=_pattern-list_ man 8 sshd]) |
|||
* '''Comment:''' Explain purpose (speeds up approval) |
|||
* Click '''Add''' / '''Hinzufügen''' |
|||
4. A new window appears. |
|||
Select '''Command''' as the usage type. |
|||
Type the full command with the full path, including all parameters, in the '''Command''' text box. |
|||
Specify a network address, list, or range in the '''From''' text field (see [https://man.openbsd.org/cgi-bin/man.cgi/OpenBSD-current/man8/sshd.8#from=_pattern-list_ man 8 sshd] for more info). |
|||
Please also provide a comment to speed up the approval process. |
|||
Click '''Add/Hinzufügen'''. |
|||
{| class="wikitable" |
{| class="wikitable" |
||
! Example: rrsync for automated data transfer |
|||
! | Example |
|||
|- |
|- |
||
| <pre>/usr/local/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/</pre> |
|||
| If you want to register a command key to be able to transfer data automatically, please use the following string as in the '''Command''' text field (please verify the path on the cluster first): |
|||
Note: Verify the exact path on your cluster first (may be <code>/usr/bin/rrsync</code>) |
|||
<pre> |
|||
/usr[/local]/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/ |
|||
</pre> |
|||
|} |
|} |
||
[[File:Ssh-com.png|center|600px|thumb|Add command SSH key to service.]] |
|||
[[File:Ssh-com.png|center|600px|thumb|Configure command key]] |
|||
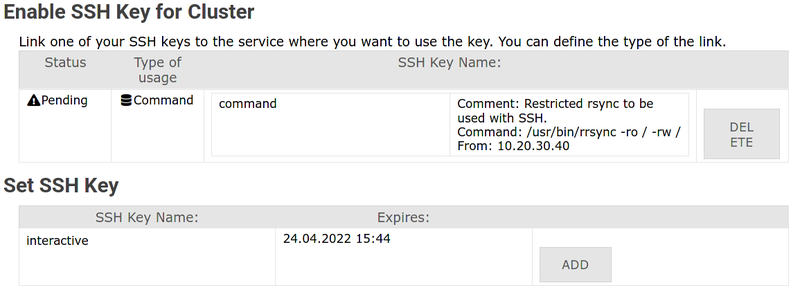
5. After the key has been added, it will be marked as '''Pending''': |
|||
You will receive an e-mail as soon as the key has been approved and can be used. |
|||
[[File:Ssh-service.png|center|800px|thumb|SSH key is now registered for interactive use.]] |
|||
'''5.''' Wait for approval: Key status shows '''Pending''' until an administrator approves it |
|||
== Revoke/Delete SSH Key == |
|||
[[File:Ssh-service.png|center|800px|thumb|Key pending approval]] |
|||
{|style="background:#deffee; width:100%;" |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
You'll receive an email when the key is approved and ready to use. |
|||
[[Image:Attention.svg|center|25px]] |
|||
|style="padding:5px; background:#cef2e0; text-align:left"| |
|||
== Revoking SSH Keys == |
|||
Revoked keys are locked and can no longer be used. |
|||
|} |
|||
Revoked keys are immediately disabled and cannot be reused. |
|||
'''1.''' Navigate to your cluster's SSH key management: |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwUniCluster 3.0'''] |
|||
* [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml '''bwForCluster Helix'''] |
|||
* [https://login.bwidm.de/user/ssh-keys.xhtml '''bwForCluster NEMO 2'''] |
|||
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys page]] |
|||
'''SSH keys''' are generally managed via the '''My SSH Pubkeys''' menu entry on the registration pages for the clusters. |
|||
Here you can add and revoke SSH keys. To revoke/delete a ssh key, please follow these steps: |
|||
'''2.''' Click '''REVOKE''' / '''ZURÜCKZIEHEN''' next to the key you want to disable |
|||
1. '''Select the cluster''' for which you want to delete the SSH key:</br> → [https://login.bwidm.de/user/ssh-keys.xhtml '''bwUniCluster 3.0''']</br> → [https://bwservices.uni-heidelberg.de/user/ssh-keys.xhtml '''bwForCluster Helix''']</br> → [https://login.bwidm.de/user/ssh-keys.xhtml '''bwForCluster NEMO 2'''] |
|||
[[File:BwIDM-twofa.png|center|600px|thumb|My SSH Pubkeys.]] |
|||
[[File:Ssh-success.png|center|800px|thumb|Revoke SSH key]] |
|||
2. Click '''REVOKE/ZURÜCKZIEHEN''' next to the SSH key you want to revoke. |
|||
[[File:Ssh-success.png|center|800px|thumb|Revoke SSH key.]] |
|||
Revision as of 18:01, 1 December 2025
|
This guide applies ONLY to: bwUniCluster 3.0 • bwForCluster Helix • bwForCluster NEMO 2 On all other clusters, SSH keys are still managed via |
Registering SSH Keys with your Cluster
SSH Keys allow you to log into a system without entering a password. Instead of proving your identity with something you know (a password), you prove it with something you have (a cryptographic key).
Why SSH Key Management?
On bwUniCluster 3.0, bwForCluster Helix, and bwForCluster NEMO 2, SSH keys must be managed through bwIDM/bwServices for security reasons:
- Security enforcement: Ensures keys use strong algorithms and have limited validity (180 days)
- Centralized management: All keys can be reviewed and revoked from one location
- Two types available: Interactive keys (for manual logins) and Command keys (for automated workflows)
Note: Self-managed ~/.ssh/authorized_keys files are ignored on these clusters.
SSH Key Requirements
Supported Algorithms and Key Sizes
- RSA: 2048 bits or more
- ECDSA: 521 bits
- ED25519: 256 bits (default, recommended)
- ECDSA-SK / ED25519-SK: FIDO2 hardware keys (Yubikey, etc.)
Important: Always protect your private keys with a strong passphrase.
FIDO2 Hardware Keys (Recommended)
|
FIDO2 SSH Keys (ECDSA-SK and ED25519-SK) offer the best security:
See SSH with Yubikey - Quick Start Guide for setup instructions. |
|
FIDO2 SSH Keys currently work ONLY on: bwUniCluster 3.0 and bwForCluster NEMO 2 NOT supported on bwForCluster Helix! |
Adding a new SSH Key
|
SSH keys are managed via the My SSH Pubkeys menu on your cluster's registration page:
1. Navigate to your cluster's SSH key management:
2. Click Add SSH Key / SSH Key Hochladen
3. Enter key details:
- Name: Descriptive name for your key (e.g., "laptop-work")
- SSH Key: Paste the complete contents of your
.pubfile - Click Add / Hinzufügen
4. Confirmation: Your new key appears in the list
Next step: Bind your key to a service as either an Interactive Key (manual logins) or Command Key (automated workflows).
Registering an Interactive Key
Interactive Keys are used for manual SSH logins to work on the cluster.
Key Validity and 2-Factor Authentication
|
Regular SSH Keys require 2-factor unlock:
FIDO2 SSH Keys (ECDSA-SK/ED25519-SK) work differently:
|
| Cluster | Validity after 2FA Login |
|---|---|
| bwUniCluster 3.0 | 8 hours |
| bwForCluster Helix | 12 hours |
| bwForCluster NEMO 2 | 12 hours |
Registration Steps
1. Add your SSH key if not already done
2. Navigate to Registered Services / Registrierte Dienste → Click Set SSH Key / SSH Key setzen for your cluster
3. Find your key in the bottom section → Click Add / Hinzufügen
4. Select Interactive as usage type → Add optional comment → Click Add / Hinzufügen
5. Done! Your key is now active for interactive logins
Registering a Command Key
Command Keys enable automated workflows without manual login (e.g., automated backups, data transfers).
Security Requirements
|
Command keys are always valid (no 2FA required), making them high-value targets. Mandatory restrictions:
|
Common use case: For rsync data transfers, see the rrsync wiki guide.
Registration Steps
1. Add your SSH key if not already done
2. Navigate to Registered Services → Click Set SSH Key for your cluster
3. Find your key in the bottom section → Click Add / Hinzufügen
4. Configure command restrictions:
- Usage type: Select Command
- Command: Enter full path and parameters (example for rrsync below)
- From: Specify IP address, range, or subnet (see man 8 sshd)
- Comment: Explain purpose (speeds up approval)
- Click Add / Hinzufügen
| Example: rrsync for automated data transfer |
|---|
/usr/local/bin/rrsync -ro /home/aa/aa_bb/aa_abc1/ Note: Verify the exact path on your cluster first (may be |
5. Wait for approval: Key status shows Pending until an administrator approves it
You'll receive an email when the key is approved and ready to use.
Revoking SSH Keys
Revoked keys are immediately disabled and cannot be reused.
1. Navigate to your cluster's SSH key management:
2. Click REVOKE / ZURÜCKZIEHEN next to the key you want to disable